Find the best Vulnerability Scanner Software
Compare Products
Showing 1 - 20 of 80 products
Sort by
Reviews: Sorts listings by the number of user reviews we have published, greatest to least.
Sponsored: Sorts listings by software vendors running active bidding campaigns, from the highest to lowest bid. Vendors who have paid for placement have a ‘Visit Website’ button, whereas unpaid vendors have a ‘Learn More’ button.
Avg Rating: Sorts listings by overall star rating based on user reviews, highest to lowest.
A to Z: Sorts listings by product name from A to Z.
Invicti
Invicti
Invicti, formerly Netsparker, is a cloud-based and on-premise solution designed to help businesses manage the entire application security lifecycle through automated vulnerability assessments. Key features include maintenance sche...Read more about Invicti
Guardz
Guardz
Guardz was specifically built to empower MSPs with the tools to holistically secure and insure SMEs against ever-evolving threats such as phishing, ransomware attacks, data loss, and user risks by leveraging AI and a multilayered ...Read more about Guardz
UserWay Accessibility Widget
UserWay Accessibility Widget
From design to deployment, UserWay makes it easier for teams to prioritize accessibility and continuous compliance. The UserWay accessibility compliance platform empowers organizations of all sizes to adhere to regulations, includ...Read more about UserWay Accessibility Widget
ESOF VMDR
ESOF VMDR
ESOF (Enterprise Security in One Framework) VMDR is the product launched by TAC Security in 2018. The product quickly assesses the risk and addresses prime concerns. ESOF VMDR is a risk-based vulnerability management platform for...Read more about ESOF VMDR
Axonius
Axonius
Axonius is an information technology asset management (ITAM) solution designed to assist small to large enterprises with monitoring inventory of software and hardware assets. It enables users to automatically validate security enf...Read more about Axonius
AppTrana
AppTrana
AppTrana is a website and application security tool, designed to help businesses manage and maintain cloud security using scanning, Pen Testing, risk detection, always-on security, WAF, traffic monitoring, and more. It provides a ...Read more about AppTrana
Syxsense
Syxsense
Syxsense is a leading Unified Security and Endpoint Management (USEM) solution that delivers real-time monitoring and intelligent automation for vulnerability management, patch management, and security remediation in a single con...Read more about Syxsense
Vulnerability Intelligence
Vulnerability Intelligence
SaaS Vulnerability Scanner is a cloud-based cybersecurity solution that features vulnerability detection, reporting tools and misconfigured service tracking for internet-facing infrastructures. SaaS Vulnerability Scanner uses...Read more about Vulnerability Intelligence
Probely
Probely
Probely is a cloud-based web vulnerability scanning solution for security teams and developers. It is suitable for companies that build digital services. The solution scans web applications and manages the lifecycle of detected vu...Read more about Probely
USM Anywhere
USM Anywhere
USM Anywhere is a cloud-based security platform which helps midsize to large enterprises with risk detection, vulnerability assessment, security monitoring and threat response. The security platform enables users to collect and ...Read more about USM Anywhere
Intruder
Intruder
Intruder is a cloud-based software designed to help businesses automatically perform security scans to identify and remediate potential threats. Professionals can proactively monitor the system, receive automated alerts about new ...Read more about Intruder
Cyber Chief
Cyber Chief
Cyber Chief offers businesses the power to identify and resolve potential vulnerabilities across web applications and cloud infrastructure. Using the one-click vulnerability scanning feature, the software helps users scan and se...Read more about Cyber Chief
Vulkyrie
Vulkyrie
Vulkyrie offers unlimited network and website security scans for small to mid-sized enterprises. A Free Plan is available for vulnerability discovery. This easy-to-use cloud-based solution helps enterprises quickly find and fix vu...Read more about Vulkyrie
HackerOne
HackerOne
HackerOne is a hacker-powered cybersecurity platform that enables organizations within the government and financial service industries to identify, capture, and resolve security vulnerabilities that were discovered by hackers. Hac...Read more about HackerOne
Qualys Cloud Platform
Qualys Cloud Platform
Qualys Cloud is a network security management software designed to help businesses monitor IT assets and prioritize threats in real-time. Administrators can receive alerts regarding vulnerabilities, suspicious activities and attac...Read more about Qualys Cloud Platform
ShiftLeft CORE
ShiftLeft CORE
ShiftLeft CORE is the only suite of Application Security tools and services capable of analyzing the complete flow of data through a modern application in minutes so dev teams can release secure code at scale. ShiftLeft can match ...Read more about ShiftLeft CORE
Security for Everyone
Security for Everyone
Your users and visitors depend on you to keep their information safe. If you want to be sure your digital assets are secure, Security for Everyone is the tool for you. With S4E, you will have: 1- Manual Vulnerability Scanning 2- ...Read more about Security for Everyone
Cyberwatch Vulnerability Manager
Cyberwatch Vulnerability Manager
Cyberwatch Vulnerability Manager helps enterprises monitor and manage vulnerabilities across servers, networks, devices and more. The platform includes a centralized dashboard, which enables organizations to gain visibility into a...Read more about Cyberwatch Vulnerability Manager
Trend Micro Cloud One
Trend Micro Cloud One
Trend Micro Cloud One is a compliance and computer security solution that helps businesses streamline processes related to threat monitoring, vulnerability scanning, behavioral analysis, file integrity monitoring, and more on a ce...Read more about Trend Micro Cloud One
Red Sentry
Red Sentry
Red Sentry is the industry leader in fast and affordable penetration testing. Our unique value comes in combining our fast pentests with our automated platform, keeping customers protected 24/7/365....Read more about Red Sentry
Popular Comparisons
Buyers Guide
Last Updated: March 16, 2023Whatever web applications, networks, servers, and systems you use for daily business operations, your network is always vulnerable to threats such as data breaches and other cyberattacks. To help avoid or combat such threats, periodic system scans using vulnerability scanner software can identify existing as well as potential network security risks.
This type of software scans your web applications, networks, systems, and environment and generates reports on identified vulnerabilities, analyzes the associated risk, and flags issues that need immediate attention.
This vulnerability scanner software buyers guide will help you differentiate between the tools on the market, compare features, and pick the right software for your business.
Here is what we’ll cover:
What is vulnerability scanner software?
Vulnerability scanner software helps IT security teams monitor web applications and networks for security threats such as malware, data breaches ransomware attacks, etc. With features including network scanning, vulnerability assessments, and web application security checks, these tools generate reports on security threats and help users prioritize riskier issues.
Vulnerability scanners run point-in-time scans to help identify vulnerabilities such as security threats, missing patches, malware, and misconfigurations. IT security teams can use it to visualize, analyze, and prioritize responses to known vulnerabilities such as poor encryption, lack of a firewall, no endpoint security, etc. These tools' functionality can be customized to reduce risk across all types of applications and networks based on your unique business requirements.
Vulnerability scanner software also helps users build and maintain a database of security vulnerability reports, which can be used to assess overall network security, track progress, and communicate potential risks to employees.
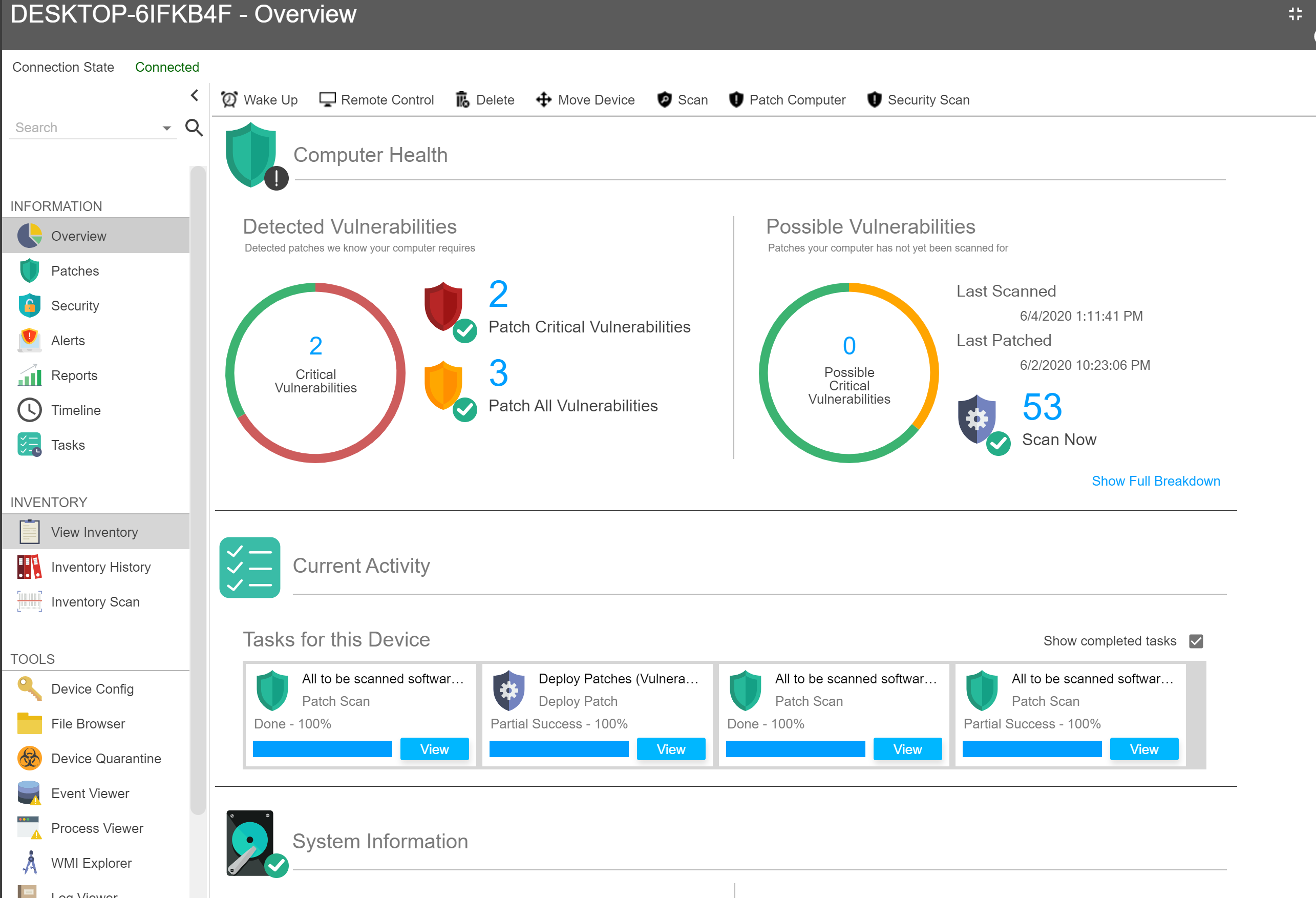
A view of the dashboard in Syxsense (Source)
Common features of vulnerability scanner software
Vulnerability assessment | Assess known vulnerabilities and potential security network threats by analyzing and classifying them based on severity. |
Network scanning | Scan networks and network-accessing assets such as servers and mobile devices to identify security threats and recommend action. |
Web application security | Identify security threats such as insecure configuration, SQL injection, and cross-site scripting (XSS) within web applications. |
Vulnerability/threat prioritization | Classify levels of threat based on severity, ease of exploitation, potential damage, and data at risk. Organize responses based on priority. |
Penetration testing (aka pen testing) | Helps test potential system vulnerabilities by enabling ethical hackers to attempt network hacks and data thievery. |
Configuration monitoring | Track misconfigurations and missing patches to rectify issues and prevent damaging hacks. |
Access controls/permissions | Regulate who can view and use the system by setting permissions and issuing strong passwords. |
API | Integrate vulnerability management features with other management solutions. |
What type of buyer are you?
The right type of vulnerability scanner tool depends on your business requirements, which are often tied to business size:
Large businesses (over 500 employees): These buyers include large organizations and enterprises that monitor a larger number of employees, systems, and networks. They usually access many applications on multiple devices. Large businesses and those that work with sensitive data (such as in the banking, government, finance, and healthcare sectors) should consider vulnerability assessment software with advanced security features and multi-device support. In addition to basic network monitoring, these buyers need features such as vulnerability assessments, vulnerability/threat prioritization, web application security, real-time alerts/notifications, internet security, access controls/permissions, and API.
Small and midsize businesses (SMB; up to 500 employees): SMBs use fewer applications, devices, and systems for their day-to-day operations. They often have more limited budgets and smaller IT teams, and are looking to ensure basic IT security for their networks and systems. SMBs that manage large amounts of customer data should consider vulnerability scanner software with features such as web application security and network scanning.
Benefits of vulnerability scanner software
Identify security weaknesses: Vulnerability scanners help you track and identify security weaknesses in your IT infrastructure by scanning networks, web applications, systems, and environments and generating reports on detected and potential vulnerabilities. Organizations can use these reports to discover and fix security issues to avoid exploitation.
Define potential risk: Regular vulnerability scanning helps determine the effectiveness of your IT security infrastructure and defines potential risks to help prevent future attacks. Scanning helps you analyze and prioritize vulnerabilities based on the level of risk involved and suggests corrective measures.
Double-check vulnerabilities: These tools double-check detected vulnerabilities to ensure that there are no false positives and save you from spending resources on non-existent issues.
Monitor network: These tools scan your networks and network-accessing devices for weaknesses such as viruses and malware. They also identify faulty web applications that might cause data theft.
Reduce costs associated with data breaches: Periodic vulnerability scans decrease your risk of falling victim to data breaches and cyberattacks, which can bring costly remediation and result in lost customer trust.
Key considerations when selecting vulnerability scanner software
Here are some important considerations to keep in mind when purchasing vulnerability scanner software:
Security requirements: Determine whether your business requires an external scanning tool to help evaluate threats from the wider internet or whether you need an internal vulnerability scan to run threat detection on your intranet. You can also choose between a comprehensive scanning option or limited scan functionality in which only assets within the network are scanned.
System compatibility: Since vulnerability scanners provide essential security and support your existing IT infrastructure, ensure that the tool you choose integrates with your other tools, systems, and networks. It should be easy to deploy and reliable, and integrate with various plugins to facilitate multi-device support, web application scanning, and network monitoring.
Reporting metrics: It's important that whatever vulnerability scanner you choose is able to generate custom, comprehensive reports about scanned networks and any identified vulnerabilities. These features should also help you analyze and categorize any issues based on the degree of risk and exploitability, and recommend corrective measures.
Pricing and budget: Budget is an important factor to consider when selecting software. Most scanners use a pricing model based on business size, the number of systems covered, type of software, and required features. Establish your budget early on to ensure that your business can afford the right tool.
Note: The application selected in this guide is an example to show a feature in context and is not intended as an endorsement or recommendation. It has been taken from sources believed to be reliable at the time of publication.







