How To Strengthen Your Healthcare Data Security With Software
Increasingly, patients choose to engage with their healthcare provider digitally. This has a lot of far-ranging implications, from new and heightened expectations placed on younger medical providers[1] to a new set of standards for patients when it comes to convenience and ease of engagement with their healthcare organization and the safekeeping of their personal data.
One other major implication of this new world we’re living in is the critical importance of healthcare data security.
According to Software Advice’s 2022 Healthcare Data Security Survey[*], 36% of healthcare organizations in the US have experienced a data breach.
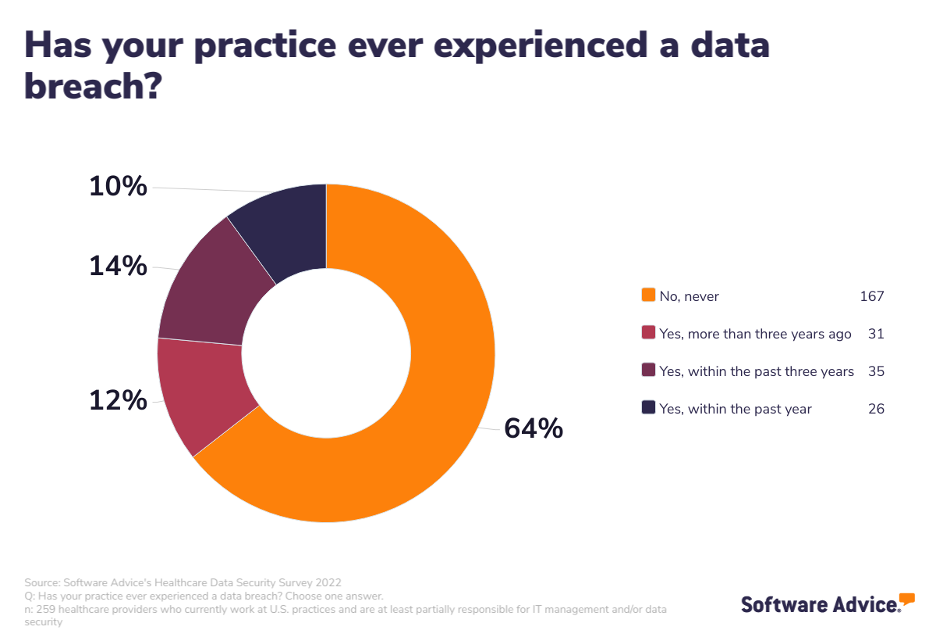
Experiencing a healthcare data breach or cyberattack is a massive blow to any medical organization, but it is exponentially more difficult to recover from if you’re a smaller, independent practice.
This is why it’s crucial for small practices to have the right data security software in place to protect your patients and your practice against data risks. In this article, we’ll cover specific HIPAA data security requirements, two types of software you should invest in to protect your data (EHRs and cloud security software), as well as specific features that make data security software so valuable.
How to meet HIPAA requirements for healthcare data security
To be compliant with HIPAA regulations, you’ve probably already established many healthcare data security standards.
According to the HIPAA Security Rule[2], healthcare entities are expected to conduct internal risk assessments in order to test their data security protocols, as well as implement security standards to protect their sensitive data.
Security programs are comprised of three distinct safeguards:
Administrative
Physical
Technical
It’s easy to get hung up on the last one since there are tons of cybersecurity systems available, but let’s take a closer look at the first two elements before diving into software.
Administrative safeguards to protect patient data
One of the most common causes of healthcare data breaches[3] is unauthorized access or disclosures. In layman’s terms, that means a data breach caused by employee error and/or negligence as well as malicious employees.
And this is pretty common. In our Healthcare Data Security Survey, we found that nearly half (49%) of the practices that experienced a data breach did so as a result of human error.
This is a great reason to install specific administrative protocols that prevent employees from mishandling patient records and medical data.
Here’s a quick summary of these administrative best practices:
Device management: Keep all computers, tablets, and mobile devices used to access patient data up to date and secure.
User-based controls: Limit who can access patient data and implement strict password protocols to hold users accountable for carefully accessing private data.
Team training: Conduct regular training and refresher sessions to ensure employees have a firm understanding of the importance of data security as well as best practices.
For a detailed look at administrative practices any healthcare organization can employ to avoid a data breach, check out “Best Practices for Avoiding HIPAA Violations in Healthcare.”
Physical safeguards to protect patient data
HIPAA requirements include physical safeguards to protect patient data.
These are defined as “physical measures, policies, and procedures to protect a covered entity’s electronic information systems and related buildings and equipment, from natural and environmental hazards, and unauthorized intrusion.”
So this element of a strong data protection plan is two-pronged:
First, you must ensure your data will not be destroyed by natural disasters such as flooding or fire. In 2021, that generally means keeping patient data secured in the cloud rather than on hard physical copies.
Second, you must have physical barriers in place to prevent unauthorized individuals from accessing your patient data. That can be as simple as having a lockable door between the outside world and the devices you use to access and record patient data. It can also mean securing those devices with strong passwords.
Software: the healthcare security heavyweight
Finally, let’s bring out the big guns and discuss the software systems that can help protect you and your patients from data security breaches. We’ll take a look at the two most important types of software to ensure data protection:
EHR security features
Using an EHR with the right security features will go a long way in keeping you and your patients’ data protected. Fortunately, most certified EHRs come with standardized features to achieve this goal. Those feature to look out for are:
ONC-ATCB certification. This means the tool has been tested on three key areas by an Authorized Testing and Certification Body that has been recognized by the Office of the National Coordinator. Those three key areas are functionality, interoperability, and security—that’s right! If an EHR is ONC-ATCB certified, that means it has passed tests confirming it has security measures in place to keep protected health information (PHI) safe.
Audit trails. This feature tracks and documents every action taken with patient information, including who accessed the data, where and when they accessed data, and what changes they made once they accessed it.
Password protection. This includes robust controls such as lockout features that will bar access if the wrong password is entered too many times and two-factor authentication to ensure the right person is using the password to access protected data.
Data encryption. Not only can data encryption make transferring patient data more secure (by only allowing recipients with the right access key to decipher the data), it can also be very helpful in the event that data is stolen as it will make it harder for the thief to actually read your data.
Read more about the most important features of secure EHRs.
Cloud security software for healthcare providers
If a secure EHR is one side of the data security software coin, cloud security is the other side.
The beauty of a cloud security system that is specifically geared toward the healthcare industry is that it automates so many processes associated with data security. For example, HIPAA requires covered entities (e.g., medical practices) to run regular risk assessments in order to identify any vulnerabilities and address them.
Most HIPAA-compliant cloud security systems are capable of running these assessments automatically. Some other common features of this type of software include:
Threat detection and response: Using analytics and other tools, software can identify attacks as they’re happening and also help users respond immediately to protect their data.
Malware protection: Software actively searches for malicious software or code, viruses, trojans, worms, etc.
File integrity monitoring: Ensures all files are secure and protected against unauthorized access or changes.
For small, independent practices that are delving deeper into the digital healthcare experience, having these robust security tools in place will go a long way to protecting patient data. They’ll also provide peace of mind, which is a valuable commodity in this day and age.
Choosing the right data security software
Some practices already have secure EHRs and cloud security systems in place. Some are working with a good EHR, but haven’t installed a cloud security system. Others are starting completely from scratch.
Regardless of your situation, it’s a good idea to run an assessment on your current software security stack to make sure your healthcare cybersecurity is covered. If you identify any gaps in your EHR security features or cloud security system, it’s wise to get those covered as quickly as possible.
When you’re ready to look further into secure EHRs or cloud security software, reach out to a software advisor by scheduling a call or chatting whenever it’s convenient for you.
Survey methodology
Software Advice conducted the Healthcare Data Security Survey in February 2022 of 259 healthcare providers who currently work at U.S. practices and are at least partially responsible for IT management and/or data security.
Sources
Rise of digital health during pandemic energises commitment and expectations of younger doctors, Healthcare IT News
Healthcare Data Security, HIPAA Journal
Healthcare Data Breach Statistics, HIPAA Journal