What Is A Session Border Controller (SBC)?
You thought the switch to VoIP would be easy…and then you found out you need a session border controller (SBC) to secure your Session Initiation Protocol (SIP) trunk.
If you don’t have an extensive background with voice networking, you’re probably scratching your head and asking yourself just what an SBC is.
SBCs are absolutely crucial to securing your voice network from malicious attacks. And that’s not an insignificant function…
The Communications Fraud Control Association estimates that toll fraud cost businesses $38.1 billion in 2015 alone.
In addition to security, SBCs perform so many other tasks that they start to seem like the VoIP equivalent of a Swiss army knife:

Victorinox Swiss Army Knife – Tinker by Andrew Toskin is licensed under CC BY 2.0
The difference is—most businesses will need many of the core SBC functions for their VoIP systems, while most of us will never find a use for the toothpick concealed within the Swiss army knife (hopefully).
This article will answer the following questions about SBCs:
(Click on a link below to jump to that section.)
What Is an SBC and Why Do I Need One?
Are SBCs Hardware or Software?
What Are the Benefits of SBCs?
What Is an SBC and Why Do I Need One?
In a single sentence, an SBC is a fancy firewall for your VoIP system.
Most vendors would balk at the sweeping oversimplification I’ve just committed. SBCs also assist your phone system in the following ways:
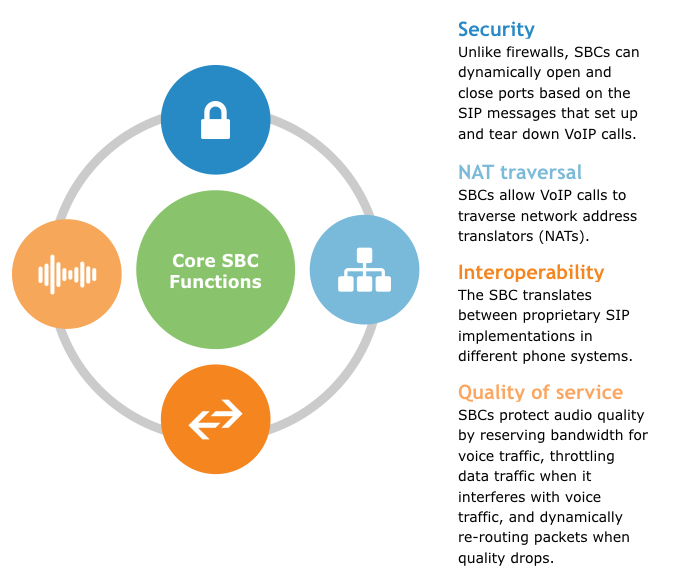
One thing probably jumps out at you when looking at the above chart—SBCs weren’t designed to be understood by the layman.
We’ve interviewed sources at a number of leading SBC vendors to help you work through some of this complexity. Before looking at the specific functions of SBCs in detail, however, we need to explain how they’re actually deployed.
Are SBCs Hardware or Software?
Again, I’m afraid I have to cheat you out of the easy answer. SBCs can be deployed in any of the following three ways:
As a dedicated physical device, installed on your business’s premises.
As a virtual machine image running on a virtualization platform such as those offered by VMware.
As a cloud-based solution offered via a cloud computing provider such as Amazon Web Services.
Many SBCs designed for smaller organizations currently on the market are hardware-based offerings.

The Sonus SBC 2000
Some businesses also choose to deploy SBCs as virtual machine images, i.e. software running on top of a virtualization platform that emulates hardware computing systems.
Historically, virtualized SBCs were deployed in enterprise data centers, but some vendors are now offering them as cloud-based solutions hosted via providers like Amazon Web Services.
SBCs are also often deployed in service provider networks, but we’re only going to focus on subscriber-side deployments here (this article is already complex enough).
So which deployment option will work best for you?
Rick Kuhlbars, CEO of FRAFOS, a provider of VoIP and WebRTC solutions including virtualized and hardware SBCs, explains that there’s no easy answer, precisely because SBCs are designed to be flexible.
“Whether you are an end user or a service provider,” he says, “you can customise your SBC deployment based on your IT strategy, be it cloud, virtual machines or hardware.”
What Are the Benefits of SBCs?
Some SBC functions are so essential to VoIP systems that they can hardly be termed “benefits.”
 Enhanced security. You might be thinking, “I’m good on security—I already have a firewall.”
Enhanced security. You might be thinking, “I’m good on security—I already have a firewall.”
The problem with firewalls is that they operate by permanently opening or closing certain ports, which is fundamentally at odds with how SIP (the network protocol that establishes and terminates VoIP calls) works. You can read more about the SIP protocol in another guide I’ve written.
Mykola Konrad is VP of product marketing and management at Sonus, a security and intelligence company for real-time communications. He explains that “SIP dynamically opens and closes ports,” i.e., each time a call is made and terminated.
Thus, if you simply close the port for good, like a firewall does, you break your VoIP system’s ability to connect calls.
But what happens if you leave the port open?
Glen Flowers is product marketing manager at Patton Electronics, a manufacturer of end-user and carrier-grade telecommunications hardware including SBCs. He explains that this isn’t exactly a smart strategy either.

“In order to allow voice traffic into your corporate LAN, you have to make what they call a ‘pinhole’ in the firewall so the voice traffic can get through. Unfortunately, snoopers and hackers looking to commit toll fraud can also find that pinhole and get through it.”
Glen Flowers, product marketing manager at Patton Electronics
The job of the SBC is to police the pinhole to make sure the traffic coming through isn’t malicious, which can result in a costly toll fraud attack or a debilitating denial of service attack.

Patton’s SmartNode 5570 Session Border Controller and Router
SBCs do this in two ways:
As Konrad notes, “an SBC has intelligence at the SIP layer, so it can tell when a session is started, and it can open up the port for the session and close it when it’s over.” Thus, you don’t have to permanently leave the port open.
SBCs also inspect the actual voice packets coming through the pinhole for signs of trouble.
Kuhlbars of FRAFOS explains, visual threat monitoring via dashboards that display activity within your SBC can help you understand how vulnerable your network is.
“Transparency is key to managing a secure network. It’s one thing to configure an SBC to be secure, but it’s another to have a visual of what’s going on in your SBC network—who’s being denied, where the denied calls are coming from, identifying behavioural patterns etc. In case there is an attack, you want your monitoring to identify and autocorrect the situation.”
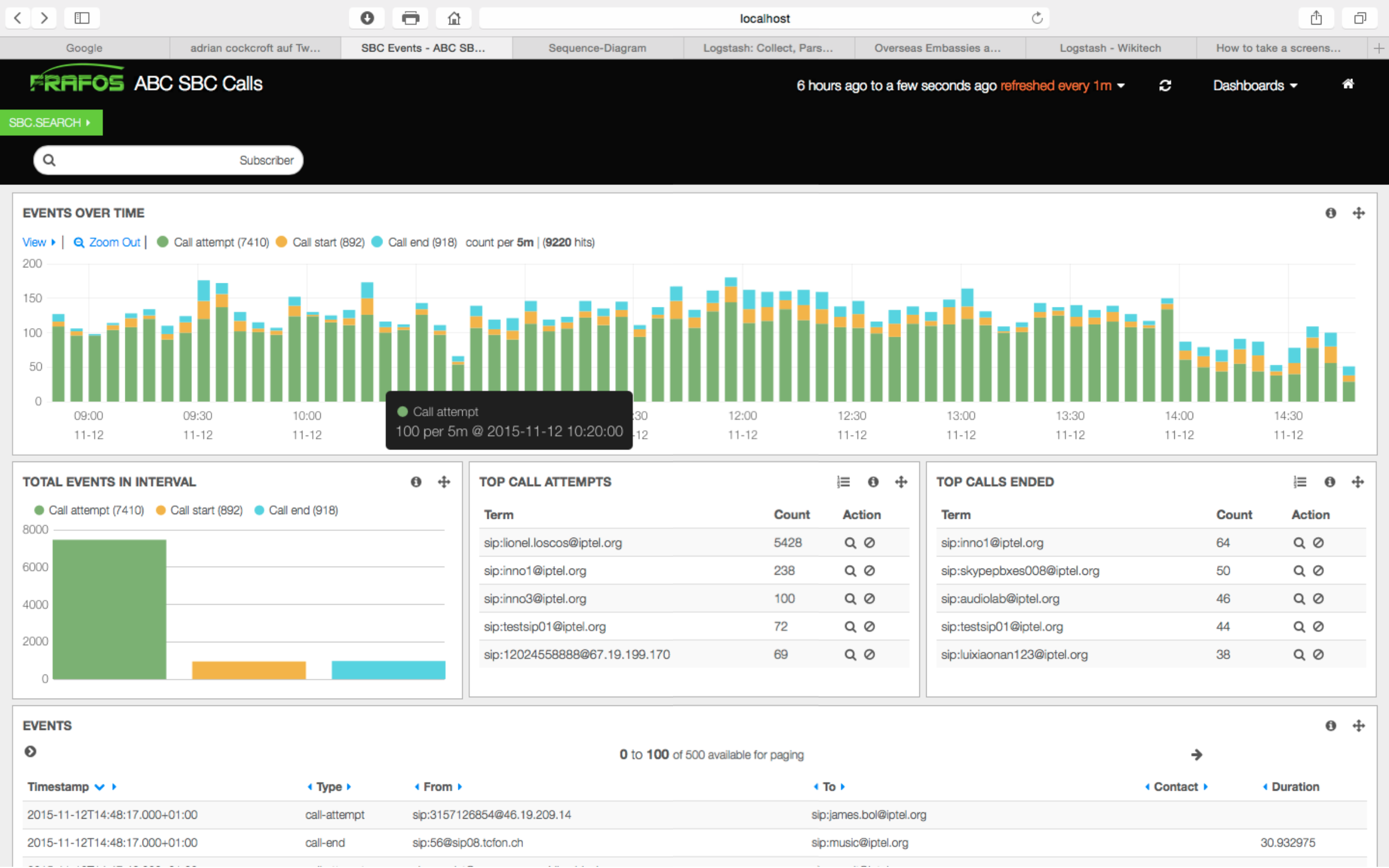
Call Attempt Monitoring in FRAFOS’s ABC SBC
The security capabilities of SBCs are evolving, as well.
As an example, Kuhlbars states that “regarding monitoring, predictive analytics is the next step for us. It will allow us to anticipate and prevent bottlenecks even more effectively.”
Predictive analytics refers to technologies that allow for the forecasting of future events and patterns based on historical data. Its most familiar usage is in business intelligence, but Kuhlbars sees potential for predictive analytics in identifying security trends and vulnerabilities.
 NAT traversal. It’s not a wise idea to expose every IP address on your corporate LAN to the public internet. So, many businesses use network address translation (NAT) to cloak many IP addresses behind a single IP address that’s exposed to the public Internet. This makes your LAN significantly more difficult to hack.
NAT traversal. It’s not a wise idea to expose every IP address on your corporate LAN to the public internet. So, many businesses use network address translation (NAT) to cloak many IP addresses behind a single IP address that’s exposed to the public Internet. This makes your LAN significantly more difficult to hack.
The problem is that SIP messages establish calls based on IP addresses, and thus have trouble connecting calls across NATs. The SBC acts as a mediator, forwarding the incoming SIP messages to the proper IP addresses on your LAN. The SBC also replaces private IP address information in outgoing SIP messages.
If you’re using NAT, an SBC isn’t a nice-to-have; it’s a must-have for a successful VoIP migration.
 Interoperability. SIP was intended to be a standard that would ensure interoperability between phone systems.
Interoperability. SIP was intended to be a standard that would ensure interoperability between phone systems.
The road to hell, unfortunately, is paved with good intentions.
Instead of one standard, we’ve wound up with a situation where many VoIP vendors offer proprietary interpretations of the standard. Avaya may use one flavor of SIP, whereas Mitel may use a different flavor.
Unfortunately, your SIP provider’s service may not be compatible with the proprietary implementation of the SIP standard in your phone system. We explain this problem in more detail in our guide to SIP trunking.
Flowers notes that this is why SBCs need to perform “SIP normalization, which involves translating between different ‘flavors’ of the SIP protocol.”
The SBC thus ensures that your phone systems play together nicely—if you have multiple systems—and, more importantly, that your phone system interoperates with your SIP provider.
 Quality of service. Most problems with VoIP calls are fundamentally caused by combining voice and data traffic over the same Internet connection.
Quality of service. Most problems with VoIP calls are fundamentally caused by combining voice and data traffic over the same Internet connection.
The packets involved in a VoIP call are time-sensitive. A tiny fragment of a word is pretty useless if it arrives five minutes after the speaker uttered it. When the Internet connection gets choked with data traffic, calls either start to sound garbled or drop altogether.
SBCs have built-in mechanisms to protect the quality of VoIP calls.
Because SBCs inspect packets, Flowers notes, they can throttle data packets when they threaten the quality of VoIP calls.
Quality of Service (QoS) mechanisms can also be found in business-grade routers. However, SBCs can perform QoS in ways that routers can’t.
For instance, Konrad observes that “the way routers do QoS is to prioritize traffic by IP address and port type. An SBC goes to a separate level, because it’s configured to look at SIP trunks, which are a logical layer on top of the network.”
“They can then look at the R-Factor to inspect the actual quality of conversations going over specific ports,” he says. “If the quality drops, the SBC can dynamically route the packets over other paths to improve quality.”
Next Steps
In many cases, SBCs aren’t sold directly. Instead, SBCs are resold by SIP providers and cloud phone system providers, or packaged with PBX hardware by hardware resellers.
Unless you already have a VoIP system in place, you should start by comparing the major brands on the market. The technical specifications of your phone system and your SIP provider’s service offering should guide your choice of an SBC.
If you’re still having trouble understanding why an SBC is necessary for your system, you may want to take a look at our guides to the SIP protocol and SIP trunking.
These guides explain the security and interoperability issues created by the fundamental characteristics of SIP messaging, which is the foundation of contemporary business VoIP solutions. SBCs were invented to solve these issues, so you may need more background on the protocol itself to understand their uses.