Find the best EDR Software
Compare Products
Showing 1 - 20 of 101 products
Sort by
Reviews: Sorts listings by the number of user reviews we have published, greatest to least.
Sponsored: Sorts listings by software vendors running active bidding campaigns, from the highest to lowest bid. Vendors who have paid for placement have a ‘Visit Website’ button, whereas unpaid vendors have a ‘Learn More’ button.
Avg Rating: Sorts listings by overall star rating based on user reviews, highest to lowest.
A to Z: Sorts listings by product name from A to Z.
ConnectWise SIEM
ConnectWise SIEM
ConnectWise SIEM (formerly Perch) is a threat detection and response management solution that allows organizations to design, deploy and manage custom cybersecurity programs. The platform includes a threat hunting functionality wi...Read more about ConnectWise SIEM
Heimdal XDR
Heimdal XDR
Heimdal eXtended Detection and Response is managed XDR solution that adds expert analysis and input from a team of cybersecurity assets to everyday endpoint detection and response approach. Heimdal XDR offers a genuinely unique ...Read more about Heimdal XDR
Blackpoint MDR
Blackpoint MDR
Blackpoint Cyber is a technology-focused cybersecurity company headquartered in Maryland, USA. The company was established by former US Department of Defense and Intelligence security experts and leverages its real-world cyber exp...Read more about Blackpoint MDR
Jamf Protect
Jamf Protect
Jamf Protect is an endpoint security solution designed to help businesses identify, prevent and resolve threats across Mac devices. The application allows users to gain visibility across remote devices and send automated alerts in...Read more about Jamf Protect
Kandji
Kandji
Kandji is the MDM worthy of your Apple devices. Set-up, visibility, and the largest library of pre-built controls — Kandji makes device management beautifully simple and insanely powerful — just the way it should be. Drawing ...Read more about Kandji
Automox
Automox
Automox is the modern, cloud-native endpoint-hardening platform that empowers organizations to remediate vulnerabilities faster than they can be weaponized. This cross-platform solution simplifies and automates critical patching, ...Read more about Automox
Huntress
Huntress
Huntress is a cloud-based cybersecurity solution, designed to help small to midsize businesses determine and respond to threats and vulnerabilities. Security teams can use the dashboard to track active incidents and investigatio...Read more about Huntress
Trava
Trava
Trava is a cybersecurity solution, which enables investors, managed service providers and businesses to identify threats, secure financial assets and assess risks. Trava's automated assessments let organizations can scan technic...Read more about Trava
JumpCloud Directory Platform
JumpCloud Directory Platform
JumpCloud Directory-as-a-Service is an IT Management software, which helps businesses of all sizes manage devices or workstations including Windows, MacOS, and Linux, access to IT resources, and user identities. The solution provi...Read more about JumpCloud Directory Platform
Netsurion
Netsurion
Netsurion Managed Threat Protection provides the necessary synergy between people, process, and technology to truly deliver world-class cybersecurity today. What does this mean to you and your business? To be covered today, you ...Read more about Netsurion
Falcon
Falcon
CrowdStrike is a cloud-based endpoint protection solution, which assists small to large businesses with anti-virus protection and device control. Key features include AI-based testing, data security and threat event detection. ...Read more about Falcon
Teramind
Teramind
Teramind offers employee monitoring, insider threat detection, and data loss prevention (DLP) solutions. Teramind UAM monitors user activities on applications, websites, file systems, network, email, social media and more. Behavio...Read more about Teramind
SentinelOne
SentinelOne
SentinelOne is a cloud-based solution that helps businesses of all sizes manage processes related to the entire threat lifecycle for providing endpoint security. Key features include behavioral analytics, activity log, whitelistin...Read more about SentinelOne
Bitdefender GravityZone
Bitdefender GravityZone
Bitdefender GravityZone is a cloud-based solution that helps businesses protect physical workstations against various cyber threats including data breaches, ransomware, phishing and more. Key features include patch management, mob...Read more about Bitdefender GravityZone
Morphisec Guard
Morphisec Guard
Morphisec is an endpoint security platform designed to help small to large businesses manage and protect devices by camouflaging applications and web browsers from malware and data intrusions. It uses moving target defense (MTD) t...Read more about Morphisec Guard
eSentire
eSentire
eSentire is a technology-enabled service provider that uses managed detection and response(MDR) services to help businesses automate processes related to threat identification, log data retention, false-positive elimination and mo...Read more about eSentire
Critical Insight
Critical Insight
Critical Insight MDR provides managed detection and response (MDR) services to businesses, allowing them to identify and mitigate potential cyber threats. By integrating machines with human intelligence, the application automatic...Read more about Critical Insight
InsightIDR
InsightIDR
insightIDR is a cloud-based security information and event management (SIEM) solution that enables businesses to streamline processes related to endpoint detection, behavior analytics, incident response and more. Professionals can...Read more about InsightIDR
Jazz Platform
Jazz Platform
Jazz Platform is a cloud-based and on-premise network security solution designed to assist small to large businesses with threat detection and response automation. Key features include data protection, image capture, forensic anal...Read more about Jazz Platform
Threat Detection Marketplace
Threat Detection Marketplace
Threat Detection Marketplace (TDM) is a SaaS content analysis platform, which provides businesses with security information event management (SIEM) and endpoint detection and response (EDR) tools to identify cybersecurity threats....Read more about Threat Detection Marketplace
Popular Comparisons
Buyers Guide
Last Updated: March 16, 2023In late 2018, global hospitality chain Marriott fell prey to a major security breach that exposed the personal information of 500 million guests. Compromised data included a combination of names, addresses, passport numbers, and dates of birth of guests. Further, hackers gained access to the credit card information of an unspecified number of guests. And although the card details were encrypted, hackers might also have stolen the information needed to decrypt these details.
Could Marriott have saved itself from landing in this mess? Yes; an endpoint detection and response (EDR) solution could have helped.
Technology advancements have paved the path for modern hacking techniques and advanced malware that can easily bypass basic anti-virus and anti-malware software. This has resulted in a need for enhanced threat protection, making EDR a necessity for all businesses. EDR tools continuously monitor business endpoints to detect vulnerabilities and protect organizations from cyberattacks.
There are many EDR software tools available on the market, and choosing the right solution for your business can be challenging. We’ve created this buyers guide to help you understand the options available for your business.
Here's what we'll cover:
What is EDR software?
EDR software is a set of tools used to detect, investigate, and analyze potential security threats in and around hosts/endpoints. It helps businesses prevent security breaches.
Endpoints are remote computing devices, such as laptops, tablets, mobile phones, and other wireless devices, that are connected to business networks. And since business networks are shared by several people, they are prone to security threats, including phishing attacks, malvertising—i.e., using online advertising to spread malware—and ransomware.
The term EDR, initially named endpoint threat detection and response, was coined in 2013 by Gartner executive Anton Chuvakin. EDR software continuously monitors endpoints and network events and records the received information in a centralized database. This information is analyzed in real time to alert businesses about suspicious activities.
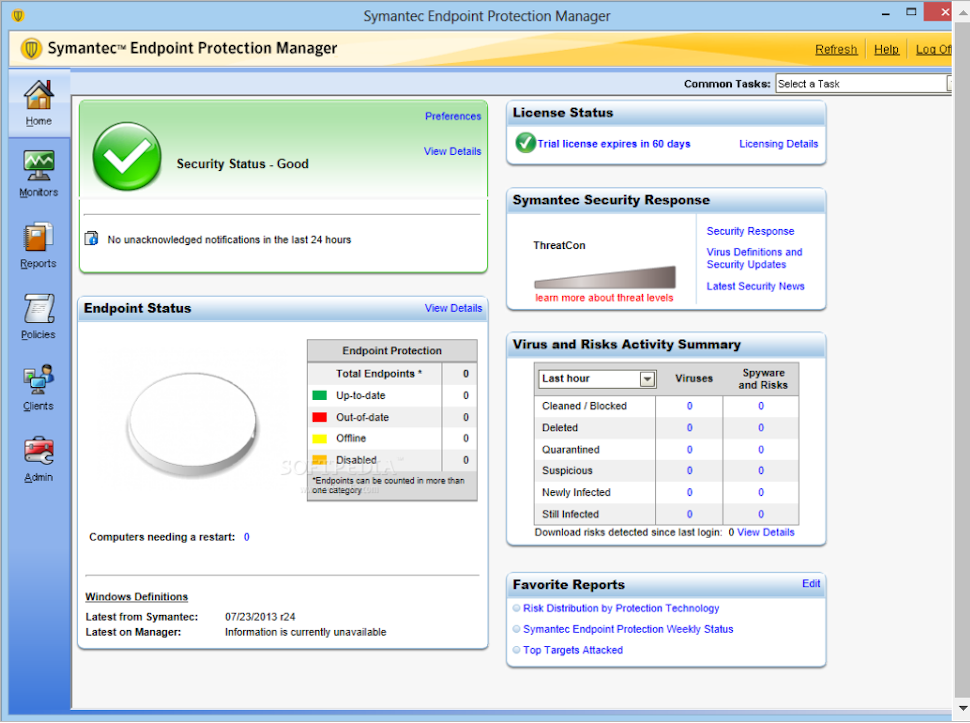
Detailed endpoint security status in Symantec Endpoint Protection (Source
Common features of EDR software
The EDR solution you choose should provide the highest level of protection against network threats and vulnerabilities. Here are some common features that you should take into account while selecting EDR software for your business.
Anomaly/malware detection | Monitor new, unexpected, or unusual network activities to detect any malware or vulnerabilities. |
Threat analysis | Identify advanced threats using behavioral analytics and machine learning technologies. |
Event analysis | Investigate security threats, detect malicious activities, and analyze such events to find ways to avoid them in the future. |
Remediation management | Remove malicious files, repair devices, and provide instructions for further actions as required. |
Route optimization | Notify administrators of suspicious activities and receive confirmation when a security incident is identified. |
What type of buyer are you?
Businesses with a higher number of employees have more endpoints to monitor. Based on the number of employees, EDR software buyers can be divided into two categories: small businesses, and midsize and large businesses. We’ll take a look at both types below.
Small businesses (less than 200 employees): In 2019, 43% of security breaches involved small businesses. As small businesses have a lower number of employees, they have fewer endpoints to secure. Most EDR software vendors charge users on a per-endpoint basis. Software that covers all network endpoints; provides visibility into hosts, files, and users; and is equipped with a wide set of remediation tools will be a good investment for small businesses.
Midsize and large businesses (200 or more employees): Over 53% of midmarket companies faced a security breach in 2018. Due to a higher number of endpoints, midsize and large businesses need higher levels of protection. Software equipped with advanced technology, such as machine learning (ML) and data analytics, can offer enhanced protection to such businesses. These software solutions can analyze data faster and automate certain remedial actions when endpoints are attacked by threats.
Benefits of EDR software
Understanding the advantages of EDR software will help you assess why your business needs one and build a strong case for an investment. Listed below are the key benefits offered by EDR software.
Higher endpoint visibility: EDR software continuously monitors all endpoints at the network level to ensure businesses don’t miss out on any potential threats. Most threats attack network blind spots, and through continuous monitoring, EDR software ensures these blind spots are highly reduced or eliminated.
Lower losses due to security breaches: Security breaches can have a massive impact on operations and result in significant losses. The average cost of a cybersecurity attack is estimated to be $1.1 million. EDR solutions collect cybersecurity events' data and analyze it in real time to identify threats and send timely alerts. These alerts assist security teams in devising risk mitigation plans that ensure threats don’t escalate into attacks, which in turn minimizes security-related losses.
Faster resolution of security breaches: EDR software accelerates the process of security breach resolution using threat detection, incident investigation, and event alerts. It stores the analysis of previous threat events, and IT experts can use this analysis to create efficient and proactive risk mitigation policies. When facing a similar attack, experts can use the available data to quickly resolve the breach, and no extra time is spent on threat investigation.
Key considerations for choosing EDR software
EDR is a key component of your organization's cybersecurity mechanism. Therefore, you must analyze all available options and their distinct capabilities to find one that is right for your security needs. Let’s go through a few key considerations that you should take into account when purchasing EDR software.
Alert filtering capability: EDR solutions that are unable to filter out false positives can lead to alert fatigue, a situation wherein monitoring professionals ignore or fail to respond to a security alert, as they deal with large numbers of alerts and consequently become desensitized to them. Alert fatigue increases the chances of critical threats being ignored and can also lead to a higher response time for threat alerts.
Role-based access: EDR software equipped with role-based access allows you to control the access rights of your system users based on their roles, such as administrator or manager. This ensures that only authorized personnel are allowed to change the configuration or settings of your EDR software, and your business remains protected from threats at all times.
Availability as a mobile application: Since EDR software monitors threats continuously, it generates a large number of alerts that need to be tracked. Missing out on any of these alerts can expose your business to a threat that could have been easily dealt with. With mobile applications, you can access threat alerts any time and from any location. Mobile applications allow you to respond to malicious threat events even while you’re on the go, thereby ensuring real-time threat protection.
If you need more detailed information about the features and benefits of EDR software, you may fill out this form for an obligation-free consultation from Software Advice. Our advisors will understand your requirements and guide you in shortlisting the most suitable options for your business.
Note: The application selected in this article is an example to show a feature in context and isn’t intended as an endorsement or recommendation. It has been obtained from sources believed to be reliable at the time of publication.