Find the best SOAR Software
Compare Products
Showing 1 - 20 of 26 products
Sort by
Reviews: Sorts listings by the number of user reviews we have published, greatest to least.
Sponsored: Sorts listings by software vendors running active bidding campaigns, from the highest to lowest bid. Vendors who have paid for placement have a ‘Visit Website’ button, whereas unpaid vendors have a ‘Learn More’ button.
Avg Rating: Sorts listings by overall star rating based on user reviews, highest to lowest.
A to Z: Sorts listings by product name from A to Z.
SIRP
SIRP
SIRP is a security orchestration, automation, and response (SOAR) software designed to help security operations centers and incident response, threat intelligence and vulnerability management teams calculate risk scores for variou...Read more about SIRP
Siemplify
Siemplify
Siemplify is a cloud-native SOAR platform designed to help security professionals automate various security processes by building playbooks using a drag-and-drop interface. Key features include playbook automation, case management...Read more about Siemplify
Swimlane
Swimlane
Swimlane is a security orchestration, automation and response (SOAR) solution, which enables enterprises in healthcare, retail, financial services and other industries to handle alerts by automating incident-response processes. It...Read more about Swimlane
Intezer Protect
Intezer Protect
Intezer Protect is a security orchestration, automation and response (SOAR) platform designed to help businesses determine potential vulnerabilities across public/private cloud environments. Supervisors can perform root cause anal...Read more about Intezer Protect
STORM
STORM
STORM is a cybersecurity software designed to help security operation centers identify, prioritize and resolve incidents. The platform enables administrators to collect and analyze cybersecurity incident-related data and automatic...Read more about STORM
IncMan SOAR
IncMan SOAR
IncMan SOAR is a cloud-based and on-premise solution, designed to helps MSSPs and organizations across finance, energy, healthcare or retail industries manage, measure, and orchestrate various security tasks such as threat hunting...Read more about IncMan SOAR
PhishER
PhishER
PhishER is a web-based Security Orchestration, Automation and Response (SOAR) platform designed to help information security and security operations teams automate the prioritization of emails and respond to threats quickly. Key f...Read more about PhishER
D3 SOAR
D3 SOAR
D3 SOAR is a cybersecurity and incident response solution that helps businesses streamline operations related to security automation, compliance management, auditing and more from within a unified platform. With the built-in visua...Read more about D3 SOAR
S.O.A.R
S.O.A.R
S.O.A.R is an endpoint detection and response software designed to help businesses detect threats to mitigate risks and prevent breaches across systems. Administrators can automatically organize and prioritize events based on tria...Read more about S.O.A.R
Cortex XSOAR
Cortex XSOAR
Cortex XSOAR is a security orchestration, automation, and response (SOAR) solution that helps businesses correlate incidents, aggregate multi-source feeds and conduct malware analysis, among other processes on a centralized platfo...Read more about Cortex XSOAR
FortiSIEM
FortiSIEM
FortiSIEM is a security Information and event management (SIEM) platform, which enables businesses to detect unusual user and entity behavior through data collection, correlation, remediation and automated response. The system mon...Read more about FortiSIEM
Cyware
Cyware
Cyware provides virtual cyber fusion centers built to enable end-to-end threat intelligence automation, sharing, and unprecedented threat response for global organizations....Read more about Cyware
CanIPhish
CanIPhish
CanIPhish is a phishing simulation and security awareness training platform that helps organizations train employees to detect and report phishing threats. The software caters to information security and IT teams in companies of a...Read more about CanIPhish
SOAR Tools
SOAR Tools
As organizations around the world face a constant and dynamic barrage of cybersecurity threats, the development of Security Orchestration tools to accelerate security operations, automation and response have rapidly increased. Th...Read more about SOAR Tools
LogPoint
LogPoint
LogPoint provides a quick analysis of your enterprise data to help businesses securely detect and respond to threats with real-time application of correlation rules. LogPoint enables organizations to identify advanced threats and...Read more about LogPoint
Orna
Orna
ORNA is a SaaS Cyber Incident Response Platform for midsize businesses, designed to replace the old-fashioned paper or PDF-based cyber incident response Plans and Playbooks. By using ORNA, businesses can effortlessly respond to th...Read more about Orna
DTonomy AIR
DTonomy AIR
Most teams receive thousands of alerts every day and large enterprises can receive millions daily. DTonomy applies AI in innovative ways to reduce false positives and recover attack stories. DTonomy's automation platform enables t...Read more about DTonomy AIR
Reveelium
Reveelium
Reveelium is a cloud-based and on-premise solution cybersecurity and safety solution that helps businesses in aviation, hospitality, IT, computer software, retail, broadcast media, and other sectors identify thefts, manage threats...Read more about Reveelium
Teleport
Teleport
Teleport is a gateway for managing access to K8s clusters, Linux & Windows servers, databases, and applications. Teleport provides access control for all your cloud resources in one place. It simplifies the management of SSH keys...Read more about Teleport
ManageEngine Log360
ManageEngine Log360
Log360 is a SIEM or security analytics solution that helps you combat threats on premises, in the cloud, or in a hybrid environment. It also helps organizations adhere to compliance mandates such as PCI DSS, HIPAA, GDPR and more. ...Read more about ManageEngine Log360
Popular Comparisons
Buyers Guide
Last Updated: March 16, 2023Your organization—be it small, midsize, or large—should always be prepared to counter cyberattacks. To ensure this, your security team uses various tools such as firewall, network security, and antivirus solutions. But managing all of these systems while simultaneously monitoring the growing number of cyberthreats can be a complicated task, and a single miss can make you the victim of an attack.
Security orchestration, automation, and response (SOAR) software helps ease this burden by centralizing data from various security tools onto a single unified platform and by automating repetitive threat detection and response processes. It collects data from all security systems, analyzes the data, and highlights incidents via alerts and notifications.
A wide range of SOAR software options is available on the market, and choosing the one that best meets your needs and budget is important. This guide will help you understand the different factors you must consider when shortlisting a SOAR solution.
Here's what we'll cover:
What is SOAR software?
SOAR software is a software tool that helps businesses automate security operations, manage threats and vulnerabilities, and respond to security incidents. It includes features such as threat intelligence, incident management, and analytics to help the security operations team identify, analyze, and counter incidents such as malware attacks and phishing scams.
The software collects data from various sources, including internal security tools, and analyzes this data to set up automated threat response workflows that can replace repetitive manual processes, such as threat hunting, data breach identification, security escalation, auditing, and stakeholder review.
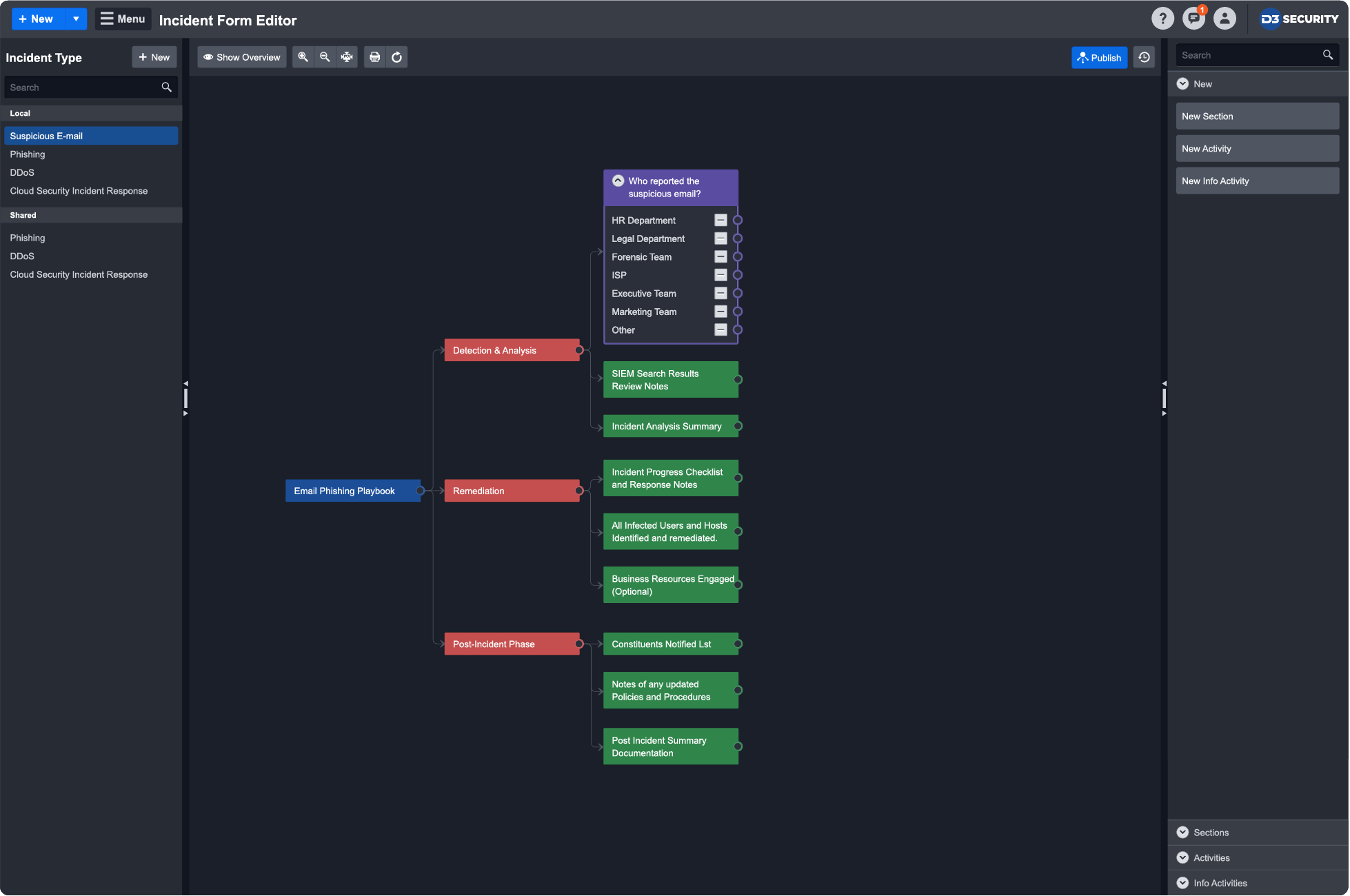
A view of the incident form editor in D3 SOAR (Source)
Common features of SOAR software
Selecting a SOAR tool is easier when you know what the most common features are and what they do. Let’s look at some common features of SOAR systems.
Incident management | Identify and manage security incidents to minimize their impact. Create a log for each security incident, investigate and analyze data related to the incident, and record details for future reference. |
Collaboration | Create workflows to communicate and escalate a potential threat or security incident to the right stakeholder. Access a centralized dashboard to stay updated on the status of security operations. |
Threat intelligence | Collect information about security threats, and get real-time alerts and updates. Analyze the collected data, share it with stakeholders for feedback, and make security modifications as suggested. |
Workflow automation | Establish security automation workflows to manage processes such as vulnerability detection, incident response, malware removal, and data breach identification. |
Performance metrics | Set benchmarks to measure metrics such as increase or decrease in security incidents over a period and the time taken to identify a breach and respond to it. Use these metrics to evaluate the overall performance of your security function. |
Reporting/analytics | Track and analyze security events and related metrics via reporting and analytics. Use relevant filters to analyze the collected data and get insights into security operations. |
What type of buyer are you?
Before evaluating SOAR software options, you should know which buyer category you belong to. Most buyers belong to one of the following categories:
Buyers looking for no-code SOAR tools: These buyers don’t have the technology infrastructure or expertise needed to write, test, and maintain custom codes for their SOAR applications. They should opt for a software tool that can automate even complex security operations using predefined automation workflows or plug-and-play capabilities.
Buyers looking for code-based SOAR tools: These buyers wish to create custom codes for their SOAR platforms so that they can modify the tool as per their needs. They also don’t mind owning the resources or hiring programmers and consultants for writing, testing, and maintaining the codes. Since maintaining such a tool will require significant investment, these buyers also have a substantial IT budget. They should opt for a code-based SOAR system that allows them the freedom to create custom codes.
Benefits of SOAR software
The key benefits of using a SOAR software tool include:
Greater operational efficiency: SOAR software improves the operational efficiency of your security team by centralizing threat monitoring and automating workflows for various processes. It helps your team collect data related to security incidents, collaborate on escalation and review processes, and share threat intelligence across departments. This lowers the chances of missing a threat alert, reduces the security incident response time, and provides your security analysts more time to diagnose the root cause of issues and make improvements.
Reduced risk: A SOAR platform sends real-time alerts about security incidents and creates automated workflows to escalate incidents to the concerned member or department. This allows your security team to take timely action and ensure immediate threat response. It also helps prioritize breaches or vulnerabilities that pose the greatest security threat.
Market trends to understand
Here’s a recent SOAR software market trend that you should know:
Increasing use of artificial intelligence (AI) and machine learning (ML) to identify data anomalies. AI and ML can help SOAR tools analyze the data coming from various security systems in real time to identify suspicious patterns or anomalies. The technology allows the incident response team to operate proactively and detect security incidents even before they take place. It also helps improve the detection of malware, phishing emails, and fraudulent payments, among others.
Having trouble finalizing software? We can help you find the right software for your needs and budget in 15 minutes or less, for free. Schedule a call or click here to chat with a software advisor now.
Note: The application selected in this article is an example to show a feature in context and is not intended as an endorsement or recommendation. It has been obtained from sources believed to be reliable at the time of publication.