Find the best Identity Management Software
Compare Products
Showing 1 - 20 of 221 products
Sort by
Reviews: Sorts listings by the number of user reviews we have published, greatest to least.
Sponsored: Sorts listings by software vendors running active bidding campaigns, from the highest to lowest bid. Vendors who have paid for placement have a ‘Visit Website’ button, whereas unpaid vendors have a ‘Learn More’ button.
Avg Rating: Sorts listings by overall star rating based on user reviews, highest to lowest.
A to Z: Sorts listings by product name from A to Z.
Persona
Persona
Persona is an identity verification management solution for businesses ranging from startups to large enterprises who need help managing the balance between customer acquisition and fraud. This solution allows users to securely co...Read more about Persona
ManageEngine ADManager Plus
ManageEngine ADManager Plus
ManageEngine ADManager Plus is an enterprise identity governance and administration (IGA) solution that helps administrators handle day-to-day AD management and reporting tasks with ease. The all-inclusive reports that can be obta...Read more about ManageEngine ADManager Plus
ManageEngine Password Manager Pro
ManageEngine Password Manager Pro
ManageEngine Password Manager Pro is an enterprise-grade privileged password management solution. It securely stores and manages sensitive information such as shared passwords, documents, and digital identities. Password Manager P...Read more about ManageEngine Password Manager Pro
OneLogin
OneLogin
OneLogin is a cloud-based identity and access management solution that helps users control access to facilities, web applications, data centers, cloud storage and more. Key features include single sign-on, web access management, a...Read more about OneLogin
Avatier Identity Anywhere
Avatier Identity Anywhere
Avatier Identity Anywhere is a cloud-based identity management solution designed to help businesses manage their employees' digital security. It includes features like password management, single sign-on, lifecycle management and ...Read more about Avatier Identity Anywhere
TeamsID
TeamsID
TeamsID is a password management solution that caters to businesses across various industries such as information technology, energy and utilities, education, financial services and more. Key features include access request manage...Read more about TeamsID
PortalGuard
PortalGuard
BIO-key PortalGuard IDaaS is a cloud-based IAM platform that offers options for multi-factor authentication, biometrics, single sign-on, and self-service password reset to support a customer’s security initiatives and deliver an o...Read more about PortalGuard
System Frontier
System Frontier
System Frontier is an identity management solution that caters to businesses in various industries such as financial services, energy and utilities, education, health care and more. Key features include access request management, ...Read more about System Frontier
Omada Identity
Omada Identity
Omada, a market leader in modern Identity Governance & Administration (IGA), provides the most comprehensive IGA as a Service solution on the market today to help organizations enable and secure all their identities. Omada Identit...Read more about Omada Identity
RapidIdentity
RapidIdentity
RapidIdentity is an identity and access management platform that provides features such as automated lifecycle management, identity governance, multi-factor authentication and password management. The solution provides role-based ...Read more about RapidIdentity
miniOrange
miniOrange
The simplest platform which integrates thousands of applications with convenient features such as SSO, MFA, Provisioning, etc. with any user source - AD, Azure AD, Okta, miniOrange. The product offers comprehensive features such ...Read more about miniOrange
LastPass
LastPass
LastPass is a password management solution for consumers and businesses that allows users to store their passwords in a digital vault. It uses single sign-on with password vaulting to protect users’ passwords. Users can save the w...Read more about LastPass
Imprivata Privileged Access Management
Imprivata Privileged Access Management
Xton Access Manager is an identity management solution that caters to businesses across various industries. Key features include access request management, role management, compliance management, single sign-on and user provisioni...Read more about Imprivata Privileged Access Management
LoginRadius
LoginRadius
LoginRadius is a cloud-based customer identity and access management solution for businesses in industries such as media, publishing, travel, nonprofit, e-commerce and sports. Key features include customer registration and authent...Read more about LoginRadius
HelloID
HelloID
HelloID is a secure and modern cloud-based Identity & Access Management (IAM) solution that empowers organizations and educational institutions to take control of their user provisioning, self-service, and single sign-on needs. Au...Read more about HelloID
Dashlane for Business
Dashlane for Business
Dashlane Business is an identity management platform for teams and businesses of all sizes. It provides access, control and an overview of organizations’ passwords and securities. The solution provides password security tools with...Read more about Dashlane for Business
Passpack
Passpack
Passpack is a web-based solution to store and organize usernames and passwords. Users can access it from any device such as mobile, tablet or PC. You can manage the credentials for both customers and staff. Itis a secure platform ...Read more about Passpack
Foxpass
Foxpass
Foxpass is a cloud-based and on-premise platform that helps small to large enterprises automate threat detection and access control process across servers and networks. It provides local cache, which enables users to keep systems ...Read more about Foxpass
Passportal
Passportal
N-able Passportal is a cloud-based solution, which helps small to large managed service providers (MSPs) automate password protection and organize relative documents. Key features include credential injection, password change mana...Read more about Passportal
Groove.id
Groove.id
Groove.id is a cloud-based access and identity management solution that streamlines account management and access control for IT and HR professionals. This solution allows professionals to automate account creation and deletion, c...Read more about Groove.id
Popular Comparisons
Buyers Guide
Last Updated: March 16, 2023You probably take a number of steps to protect your identity on a day-to-day basis. Your bank accounts, utilities accounts and even your social media accounts are all password-protected to make sure nobody but you can access them. You're wise to do this, because in today's world to have your identity stolen online means suffering a great deal of havoc that might take you months, if not years, to correct.
So why should you be any less careful when it comes to identity protection at your small-to-midsize business (SMB)? It can be just as dangerous and disastrous in your business life as in your personal life if an unauthorized person should gain access to your SMB's private information.
That's where identity management software comes in.
Identity management software manages who within your company can access information, keeping out unauthorized users as well as specifying levels of access for different individuals.
This guide will explain what you need to know about this software, and what you need to consider when choosing the right identity management system for your SMB.
Here's what we'll cover:
What is Identity Management Software?
Common Features of Identity Management Software
What is Identity Management Software?
Identity management software plays a massive role in the overall cyber-security of your SMB. It can be used to provide access to vital information, documents and other content for specific employees, while keeping others restricted to a lower level of access. In addition, it ensures that everyone granted any access is actually whomever they say they are.
More generally, identity management is the process of controlling information about users on computers, including the information that authenticates user identity and grants/limits authorization to each individual user.
Identity management software is particularly important in a business environment where so much important data and information can be accessed by a large variety of stakeholders independently.
In order to make sure that the people who need that information are able to get to it when they need to do so, while at the same time preventing outside forces from finding or accessing that information, identity management is a requirement of any modern business operation, including SMBs like yours.
Other terms that you may see used interchangeably for “identity management systems" include:
Access governance systems
Identity and access management systems
Entitlement management systems
User provisioning systems
Common Features of Identity Management Software
Below is a table listing some of the most common features of identity management software. Most of these features relate to how access is granted and/or restricted to certain users, and different vendors and systems may utilize different methods to this end:
Access Control | Creates a gated wall that must be surpassed in order to access certain information. As a result, access can be authorized or restricted for certain persons across different locations and systems, allowing the right people to gain access to information and keeping the wrong people from getting their hands on that information. This is the core functionality of identity management software. |
Single sign-on (SSO) | Allows users to log into a system just one time (rather than multiple times over the course of a session) using a single ID and password. The user may move between different connected systems once they have signed on, but they don't need to enter a new ID/password (or re-enter the same one) in order to do so. |
Multi-factor authorization | Asks for multiple, independent data components from a user before they can gain access to the system. Typically this requires a user to both enter their password as well as an encrypted, randomly generated code, created on demand when they enter that password and sent to them via text message or email. |
Password management | Assists users in generating complex passwords (either by storing them in an encrypted database or creating them on demand) and retrieving lost or forgotten passwords. This function will also typically provide self-help to users who are having trouble signing in. |
Directory Services | Creates a central point from which access can be managed by administrators, granting certain users specific levels of access to data (and restricting all others from accessing that same data). |
Multi-factor authorization will frequently require users to provide an independent form of verification, such as a separate email address or a phone number. That text message authentication may look something like this:
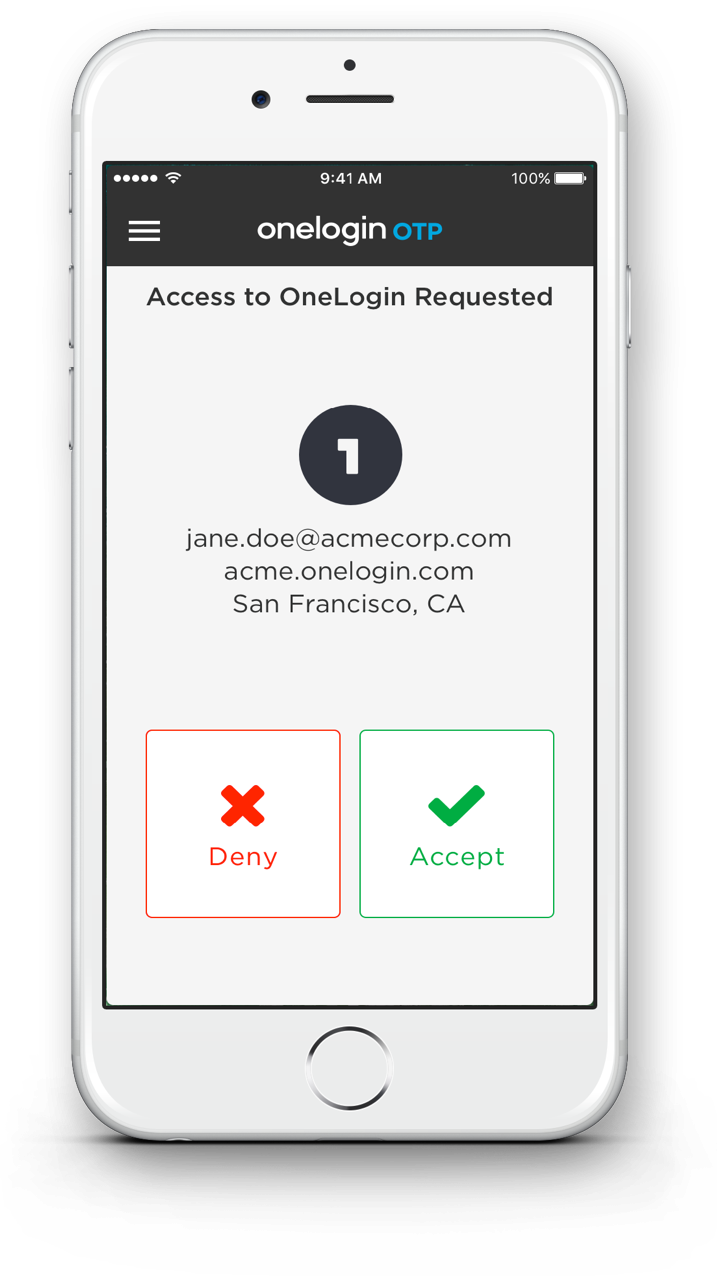
Onelogin's multi-factor “adaptive authentication", sent via text message.
Key Considerations
Other factors to take into consideration when picking the best identity management software for your business include:
Will my users require varying levels of access? At larger, enterprise-level companies, a key component of identity management software is the functionality that grants/restricts access to certain information for certain individuals. Your much smaller SMB may not have the same need to restrict information. If you only have a handful of employees who all have equal access to your data, for example, you may be able to purchase a simpler, cheaper identity management system that doesn't allow you to create restrictions.
Do I want a single sign-on system? If you're more concerned with security than you are with ease of use for your employees, then you may not want to use an SSO system, thus requiring users to enter IDs and passwords at multiple times during their journey through the system. This can be a major annoyance, however; for this reason, most identity management software vendors provide SSO as their main offering.
Do I want a multi-factor system? If you want to make sure your system is secure, you should look for a multi-factor system that will require users to have both their password and access to a backup form of identification (like a separate email address or a phone number to which an access code can be sent).
Does this system integrate with my other software? Creating a gateway to your company's database/intranet/internal systems is only useful if that gateway can actually connect to the software that you're already utilizing. Many of these systems have their own forms of identity management already built in, so you'll want to have an in-depth discussion with your vendor about how their identity management product will fully integrate with all your other software systems.