FastPass IVM
About FastPass IVM
FastPass IVM Pricing
Please contact vendor for pricing details.
Free trial:
Not Available
Free version:
Not Available
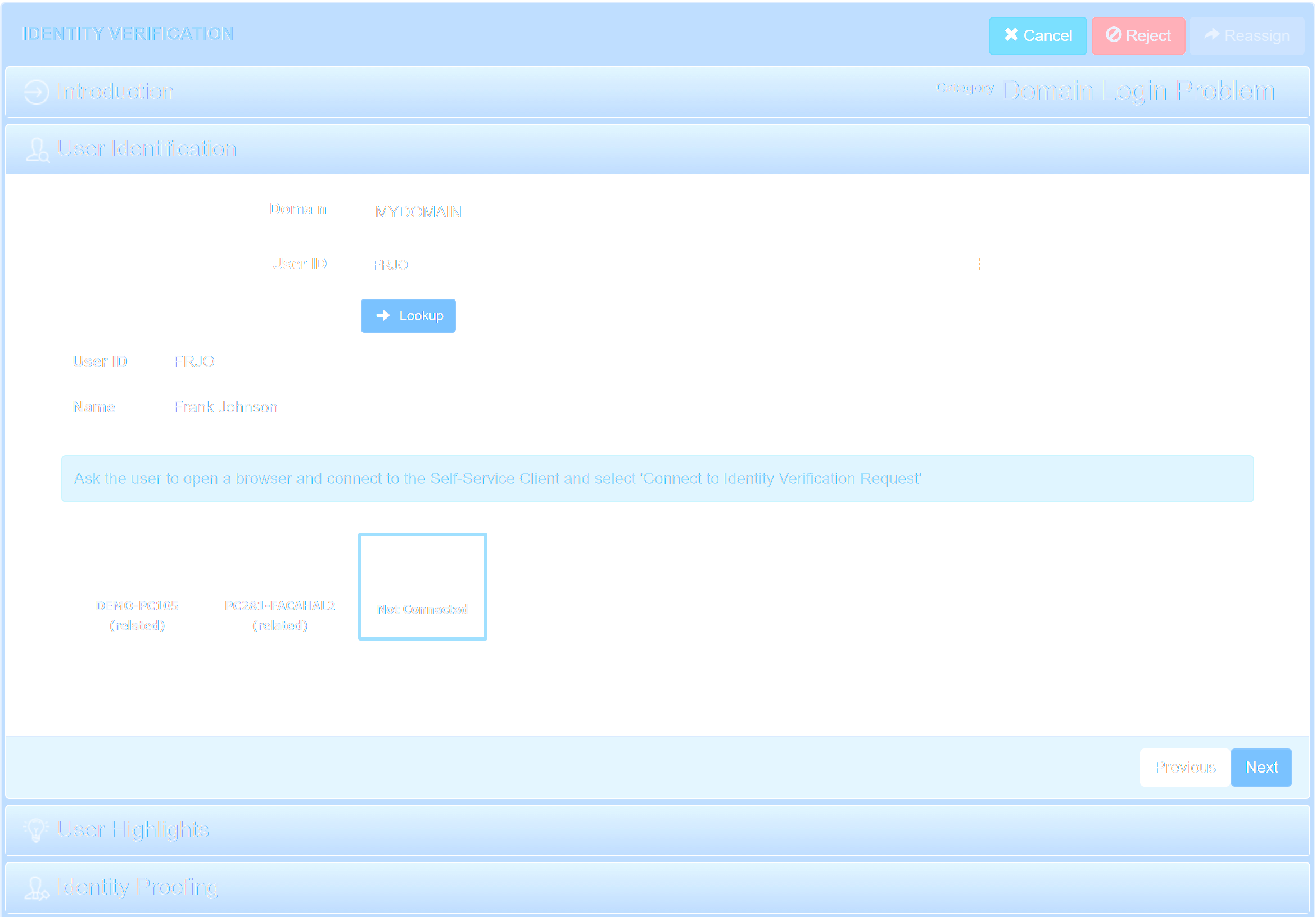
Most Helpful Reviews for FastPass IVM
1 Review
Almero
Information Technology and Services, 51-200 employees
Used daily for less than 2 years
OVERALL RATING:
4
EASE OF USE
4
VALUE FOR MONEY
5
CUSTOMER SUPPORT
5
FUNCTIONALITY
5
Reviewed January 2024
FastPass IVM is an effective way to secure helpdesk interactions
FastPass IVM provides a "polite" way of introducing identity verification as part of an helpdesk interaction. This builds trust between both parties that services can be effectively rendered. It is as simple as possible since in most cases this can be seamlessly (as much as is allowed) integrated into the ITSM tool of choice.
CONSThe initial learning curve on process configuration can be intimidating. Luckily there are sample setups that can be cloned or used, and verification processes can be designed to be simple at first and then be expanded as the company matures.
