Find the best Access Governance Software
Compare Products
Showing 1 - 20 of 95 products
Sort by
Reviews: Sorts listings by the number of user reviews we have published, greatest to least.
Sponsored: Sorts listings by software vendors running active bidding campaigns, from the highest to lowest bid. Vendors who have paid for placement have a ‘Visit Website’ button, whereas unpaid vendors have a ‘Learn More’ button.
Avg Rating: Sorts listings by overall star rating based on user reviews, highest to lowest.
A to Z: Sorts listings by product name from A to Z.
ManageEngine AD360
ManageEngine AD360
ManageEngine AD360 is an integrated identity and access management solution that assists organizations to manage and secure user identities, facilitate identity governance, and ensure compliance. It provides in-depth access manag...Read more about ManageEngine AD360
Zilla Security
Zilla Security
Zilla Security is an early-stage security startup that provides software-as-a-service security management platform....Read more about Zilla Security
Satori
Satori
Satori is a Data Security Platform (DSP) that enables self-service data and analytics. Unlike the traditional manual data access process, with Satori, users have a personal data portal where they can see all available datasets and...Read more about Satori
NordPass Business
NordPass Business
NordPass Business — The Ultimate Password Manager for Your Organization. Trusted by businesses worldwide, NordPass Business offers a cutting-edge, zero-knowledge security architecture password management solution for businesses o...Read more about NordPass Business
Netwrix Privilege Secure
Netwrix Privilege Secure
Netwrix is a cloud-based access management software that can help users minimize the risk inherent in privileged accounts. Implement a zero standing privilege approach and create on-demand accounts with just enough access to perfo...Read more about Netwrix Privilege Secure
IDHub
IDHub
IDHub is a fully customizable, flexible, and user-friendly IAM solution. We know managing a highly technical IAM system can be challenging. However, convincing users how and why to use it is often as difficult. After nearly two de...Read more about IDHub
YESOD
YESOD
YESOD is a business management platform designed for Japanese companies with multiple departments. YESOD allows founders and employees to access necessary information from a central location by switching the dates for past and pre...Read more about YESOD
Def-COMS
Def-COMS
Def-COMS is an encryption platform that helps secure communications including voice, conference and video calls, instant messaging and email. With Def-COMS we encrypt all user communication with communication partners as well as w...Read more about Def-COMS
The OptimalCloud
The OptimalCloud
The OptimalCloud is an identity and access management solution designed to help enterprises handle access to various applications using single sign-on (SSO) authentication technology. The platform includes audit trails, which enab...Read more about The OptimalCloud
NetIQ
NetIQ
NetIQ is an access management product portfolio that helps organizations share confidential information across web and cloud environments. Capabilities include single sign-on, multi-factor authentication, self-service password res...Read more about NetIQ
SailPoint
SailPoint
From the most sophisticated identity technologies to the scale to support complex, global enterprises, SailPoint leverages a common set of services to power our AI-driven Identity Security Cloud solutions and provides speedier del...Read more about SailPoint
Avatier Identity Anywhere
Avatier Identity Anywhere
Avatier Identity Anywhere is a cloud-based identity management solution designed to help businesses manage their employees' digital security. It includes features like password management, single sign-on, lifecycle management and ...Read more about Avatier Identity Anywhere
Auth0
Auth0
Auth0, a product unit within Okta, takes a modern approach to identity, enabling organizations to provide secure access to any application, for any user. The Auth0 Identity Platform is highly customizable, as simple as development...Read more about Auth0
OneLogin
OneLogin
OneLogin is a cloud-based identity and access management solution that helps users control access to facilities, web applications, data centers, cloud storage and more. Key features include single sign-on, web access management, a...Read more about OneLogin
JumpCloud Directory Platform
JumpCloud Directory Platform
JumpCloud Directory-as-a-Service is an IT Management software, which helps businesses of all sizes manage devices or workstations including Windows, MacOS, and Linux, access to IT resources, and user identities. The solution provi...Read more about JumpCloud Directory Platform
Access Rights Manager
Access Rights Manager
Access Rights Manager is a Windows-based access management tool that assists network security teams with directory monitoring and custom reporting. It is primarily designed to scan file servers, provide role-specific templates on ...Read more about Access Rights Manager
Appsian Security Platform
Appsian Security Platform
Appsian Security Platform is a cloud-based solution designed to help organizations manage data access, user authentication, network security, and other operations for PeopleSoft and SAP applications. The platform includes a transa...Read more about Appsian Security Platform
Ermetic
Ermetic
Holistic security for AWS, Azure and GCP Tenable's holistic cloud infrastructure security platform reveals and prioritizes security gaps in AWS, Azure and GCP, and enables you to remediate immediately. From full asset discovery ...Read more about Ermetic
SecurEnds Identity Governance and Access Control
SecurEnds Identity Governance and Access Control
SecurEnds is an identity management and security compliance solution that allows businesses to automate internal audits for credential access and manage access control for users within the system. With SecurEnds, Businesses are ab...Read more about SecurEnds Identity Governance and Access Control
Freedom Cloud ACaaS
Freedom Cloud ACaaS
Freedom Cloud is a cloud-based access control solution, which helps businesses of all sizes across government, education, aviation and various other industries manage, monitor and maintain physical access control systems. Freedo...Read more about Freedom Cloud ACaaS
Popular Comparisons
Buyers Guide
Last Updated: March 27, 2023An increase in the number of cyberattacks and data privacy regulations has made compliance a necessity for businesses across industries. Companies, such as yours, are becoming more aware of the risks and costs associated with insider threats. For instance, do you know who has access to which resources within your organization? Does an employee have access to information they shouldn’t have?
If such security concerns are increasing pressure on your IT and business managers, an access governance solution can help. Access governance software can mitigate security risks by providing complete visibility into the business resources your employees can access. It lets you monitor and control user access rights to the systems and applications used within your organization.
There are many access governance solutions available on the market, but one size doesn’t fit all. We have created this buyers guide that has all the information you’ll need to make the right software choice for your business.
Here’s what we'll cover:
What is access governance software?
Access governance software, also known as identity management software, is a tool that helps IT teams track, audit, and control which users have access to company resources. It verifies the identity of employees before granting them access to IT and business resources such as computer systems, software applications, data, and networks.
An access management solution aims to increase enterprise security by reducing instances of unauthorized access. It lets you configure user access rules or policies based on parameters such as employee role, function, or department. You also have an option to revoke access rights for any user at any given time.
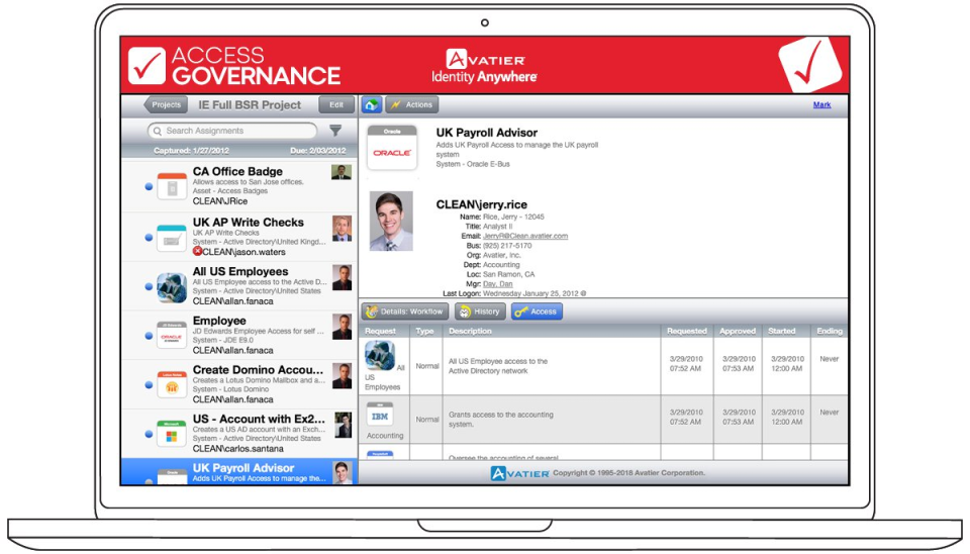
Access governance in Avatier Identity Anywhere (Source)
Common features of access governance software
Access certification | Verify access rights to ensure every user has appropriate authorization to use IT and business resources. |
Identify violations to access policies and analyze approval logs to ensure your business is complying with all regulatory mandates. | |
Real-time reporting/analytics | Monitor user activity in real time, and get in-depth details about who accessed what, when, and from where. |
User provisioning | Create, modify, disable, and delete user profiles and the associated rights to access IT and business resources. |
Multifactor authentication | Ensure employees are verifying their identity by providing at least two sets of credentials, such as username and password and mobile OTP, before getting access to company resources. |
Generate and store passwords in a centralized encrypted database, and assist users in retrieving lost or forgotten passwords. | |
Self-service access request | Allows users to complete certain actions on their own, such as resetting forgotten or expired passwords and updating basic account information. |
Role-based access control | Grant access rights to business applications, networks, and other resources based on a user’s role, job function, or department within the organization. |
Privileged access management | Assign privileged access rights to certain users based on their role or job function. Such rights can include admin permissions, the ability to edit documents, and the right to delete user accounts. |
Remote access management | Remotely monitor and control user access to computer systems, networks, files, and other company resources. |
Single sign-on | Allow your employees to use a single set of credentials to access all business applications, systems, and other resources. |
Secure endpoint devices such as PCs, laptops, and cellphones from unauthorized user access. |
What type of buyer are you?
Before purchasing an identity management solution, you should assess your business needs to understand which buyer category you belong to. The majority of buyers fall into the following categories:
Small and midsize enterprises (up to 500 employees): Small and midsize businesses (SMBs) need access governance to ensure security for internal systems and applications, manage passwords, and keep sensitive data safe from unauthorized use. Due to limited IT resources and budget constraints, these issues usually go unaddressed or become time-consuming to manage, resulting in issues such as data breaches and loss of sensitive information
To mitigate these issues, SMBs should opt for a budget-friendly access governance solution with features such as user provisioning, access certification, password management, and employee self-service to reduce the IT workload as well as administrative expenses. A cloud-based tool would also benefit these buyers, as it would allow them to scale operations as their business grows in size.
Large enterprises (over 500 employees): Large enterprises have complex operations and handle multiple systems, applications, files, and other resources. Thus, they need to assign different levels of access privileges to different departments or employee roles. The IT teams of such organizations have to continuously monitor user access activities to identify anomalies and take immediate risk mitigation steps.
A full-featured access governance solution that also offers user identity management capabilities would be a good fit for these buyers. They should also opt for an access request management tool that helps ensure compliance with data privacy regulations such as the Data Protection Act and GDPR.
Benefits of access governance software
Deploying an access and identity management system can offer many benefits. Let’s take a look at the main ones.
Comprehensive view of roles and privileges: The software lets you view all active user accounts and the privileges assigned to them. This provides clarity into each user function and role. The insights provided by the tool also help you understand how company resources are being used by different users. You can monitor resource misuse or underutilization and take the necessary remediation steps.
Data-backed decision-making: The reporting and analytics feature of the tool provides IT admins a clear picture of how employees are using their access rights. You can generate reports on risk indicators, user behaviors, access patterns, and much more to identify suspicious activities or inappropriate usage. Thus, you’re better equipped to make decisions about modifying access rights or taking immediate steps to address issues.
Better compliance management: The software lets you verify user access rights to ensure your business is compliant with the security and privacy requirements of industry regulations such as GDPR and SOX. The tool’s access certification feature allows you to establish consistent, reliable practices for periodic audits. It also continuously monitors compliance policies to ensure your security measures are up to date with regulatory requirements.
Improved security: With complete visibility into user access rights, you can detect policy violations or compromised identities in real time. You can also identify dormant accounts and entitlement creeps—i.e., if employees have more access than required for their job. Thus, the system helps you secure your business resources from unauthorized users and potential frauds.
Market trends to understand
Here’s a market trend to keep in mind when selecting an access governance software solution for your business:
Intelligent AI-driven analytics is leading to better access control and identity governance. Today, even non-human identities such as bots and IoT devices can access business systems and resources, increasing the risk of identity frauds. Organizations need to recognize where and how these identities are used in the IT infrastructure to ensure there are proper procedures to manage the access rights assigned to them. AI-driven analytics can help mitigate the potential risks arising from such non-human identities by using intelligent analytics to streamline the user provisioning process. In line with this trend, software vendors are expected to introduce AI-driven access control functionality in their offerings.
Note: The application selected in this article is an example to show a feature in context and is not intended as an endorsement or recommendation. It has been obtained from sources believed to be reliable at the time of publication.