Find the best Digital Forensics Software
Compare Products
Showing 1 - 20 of 23 products
Sort by
Reviews: Sorts listings by the number of user reviews we have published, greatest to least.
Sponsored: Sorts listings by software vendors running active bidding campaigns, from the highest to lowest bid. Vendors who have paid for placement have a ‘Visit Website’ button, whereas unpaid vendors have a ‘Learn More’ button.
Avg Rating: Sorts listings by overall star rating based on user reviews, highest to lowest.
A to Z: Sorts listings by product name from A to Z.
Cyber Triage
Cyber Triage
Cyber Triage is an automated incident response software designed to help businesses collect and analyze relevant data after an alert is generated. Key features include malware detection, memory image analysis, Yara rules, threat t...Read more about Cyber Triage
Harmony Endpoint
Harmony Endpoint
Harmony Endpoint is a cloud-based and on-premise security and digital forensics solution, which helps small to large businesses ensure protection from malware, ransomware or phishing attack. Features include threat hunting, real-t...Read more about Harmony Endpoint
DomainTools
DomainTools
DomainTools is a web-based threat intelligence software designed to help businesses assess the risk of domains, investigate online fraud and cybercrimes, manage phishing detection and monitor infringing activity. Key features incl...Read more about DomainTools
Magnet AXIOM
Magnet AXIOM
Magnet AXIOM is a Digital Forensics software for Public Safety professionals designed to recover and examine evidence in a case file. The platform allows administrators to retrieve data such as browser history, deleted files and ...Read more about Magnet AXIOM
Trellix Network Security
Trellix Network Security
Trellix Network Security is an on-premise and cloud-based solution designed to help businesses leverage artificial intelligence (AI), Multi-Vector Virtual Execution (MVX) and machine learning (ML) technologies to detect, manage an...Read more about Trellix Network Security
Lima
Lima
Lima is a digital forensics solution, which enables regulatory bodies, law enforcement agencies and businesses to manage forensic cases of all types. Professionals can create auditable notes to maintain compliance with quality sta...Read more about Lima
MailXaminer
MailXaminer
The first major launch in the field of e-Discovery applications, led by MailXaminer, was a complete forensic email investigation and analysis tool, a complete toolkit for recording, analyzing, checking and reporting email evidence...Read more about MailXaminer
Barracuda Forensics and Incident Response
Barracuda Forensics and Incident Response
Barracuda Forensics and Incident Response is an email security solution that helps businesses identify and respond to email attacks. The platform allows employees to automate operational processes, analyze the nature and scope of ...Read more about Barracuda Forensics and Incident Response
Intercept X Endpoint
Intercept X Endpoint
Sophos Intercept X is a hybrid antivirus solution that provides businesses protection against malware, viruses and offers a remote management tool. The anti-malware protection is designed to identify, block or remove threats, thus...Read more about Intercept X Endpoint
CyFIR Investigator
CyFIR Investigator
CyFIR Investigator is an endpoint detection and response solution, which enables businesses to identify and respond to cyber threats across computer networks. Managers can remotely investigate internal issues related to sexual har...Read more about CyFIR Investigator
Forensic Toolkit (FTK)
Forensic Toolkit (FTK)
Forensic Toolkit (FTK) is an investigation management software designed to help businesses in the healthcare, finance, legal, energy and other sectors search, process and index data from multiple sources. The platform enables admi...Read more about Forensic Toolkit (FTK)
D3 SOAR
D3 SOAR
D3 SOAR is a cybersecurity and incident response solution that helps businesses streamline operations related to security automation, compliance management, auditing and more from within a unified platform. With the built-in visua...Read more about D3 SOAR
Detego Digital Forensics
Detego Digital Forensics
Detego Digital Forensics is designed to help intelligence agencies, law enforcement units, and forensic departments analyze and extract data from various online and external storage devices. It allows organizations to capture and ...Read more about Detego Digital Forensics
E3:Universal
E3:Universal
E3:Universal is an on-premise digital forensics solution, which helps investigators and businesses in the public sector process multiple types of evidence from within a unified platform. Professionals can utilize the content analy...Read more about E3:Universal
EnCase Forensic
EnCase Forensic
EnCase Forensic is a digital forensic solution that can collect and preserve critical desktop/mobile evidence from multiple sources such as text messages, call records, pictures, graphics, and much more. Using OCR and image anal...Read more about EnCase Forensic
Aware
Aware
The Aware platform enables organizations to proactively discover, classify, secure, and manage data It solves for governance, risk, compliance and insights from collaboration tools like Slack, Workplace, Teams, and Yammer. Aware s...Read more about Aware
IBM QRadar Incident Forensics
IBM QRadar Incident Forensics
IBM QRadar Incident Forensics is a digital forensics solution that helps businesses streamline operations related to data collection, rebuilding, analysis, and more on a centralized platform. It enables staff members to gain visib...Read more about IBM QRadar Incident Forensics
Trimble Forensics Capture
Trimble Forensics Capture
Trimble Forensics Capture helps investigators map crime scenes and collect data faster with guided workflows. The guide, made up of a series of step-by-step instructions, can be customized by your organization to fit the needs of ...Read more about Trimble Forensics Capture
LeaksID
LeaksID
Companies all over the world may cooperate and share documents safely with LeaksID. Every time a user accesses a document, their name and the date of access are added to every word and component. The marks cannot be removed becaus...Read more about LeaksID
Caseboard
Caseboard
Caseboard is a solution specialized in data integration and analysis, whose functionalities improve the processes of criminal investigation, auditing, prevention and the fight against fraud. Based on interaction with various secu...Read more about Caseboard
Popular Comparisons
Buyers Guide
Last Updated: March 16, 2023Technological advances mean more sophisticated attacks on devices such as smartphones and laptops. These days, most business and personal transactions are performed electronically, and confidential data is stored on network drives and in the cloud. What happens, then, if your data is stolen or deleted? How will you retrieve the lost information, secure your data in the future, and determine the cause of the breach?
Digital forensics software can help with these and other cybersecurity concerns. These tools aid efforts to collect and preserve evidence, and analyze digital footprints found on devices/in a system after a data breach. Digital forensics software lets you recover data from devices, read encrypted files, and document evidence as needed in response to cybersecurity attacks.
Digital forensics software is closely related to network monitoring and investigation management software. Understanding the differences between these tools and selecting the right fit for your business can be overwhelming. Don't give up; this digital forensics software buyers guide has all the information you need to choose the right software for your organization's needs.
Here’s what we’ll cover:
What is digital forensics software?
Digital forensics software can be used within your IT system to collect digital evidence (in the form of documents, files, records, or data) to determine the cause of security incidents. These tools are used to identify, collect, preserve, analyze, interpret, document, and present evidence gathered from hardware or network logs to recreate security incidents on an electronic device or determine how a device was used to commit a crime.
Digital forensics tools can specialize in specific areas, including database forensics, email analysis, network analysis, memory forensics, disk and data capture, computer forensics,and file analysis. Some tools offer functionality in multiple areas, essentially providing a single toolkit to address varied digital forensics needs.
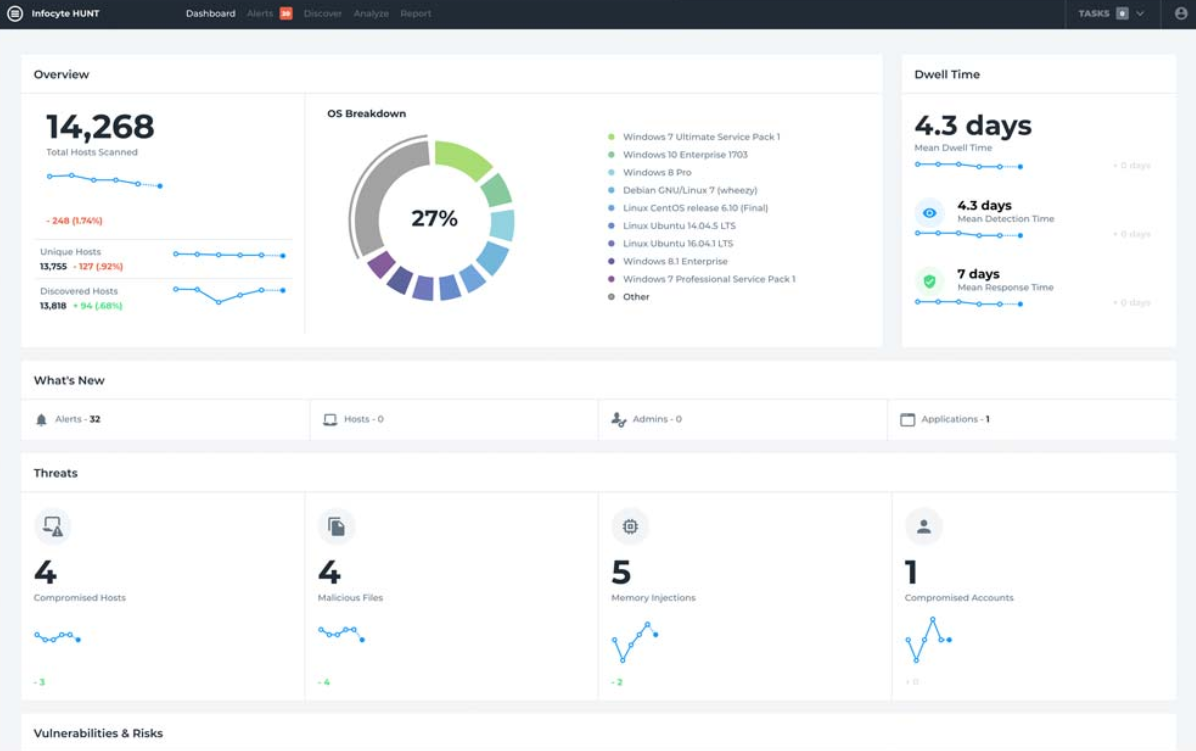
Reporting in Infocyte Software (Source)
Common features of digital forensics software
Track and capture data from multiple sources so you can quickly search, identify, and prioritize potential evidence for cybercrime investigations. | |
Data management | Acquire, validate, store, protect, and process data including system logs, application logs, user authentication logs, and database logs in one location. |
Evidence management | Collect, document, and secure evidence in a centralized platform for easy access and sharing with investigators. |
Reporting/Analytics | Generate easy-to-read and interactive reports for legal proceedings. |
Data/File recovery | Recover data and files that were lost or deleted as a result of cybercrime or unauthorized access. |
Incident response | Define a set of policies and procedures to quickly identify, contain, and respond to cyberattacks. |
Track network aspects such as traffic, bandwidth utilization, uptime, and performance. This can help users monitor anomalous traffic, and analyze email or chat sessions to identify intrusions and insider threats. | |
Computer and mobile device acquisition | Acquire data from a variety of devices including computers and mobile devices such as smartphones, tablets, and GPSs. |
Decryption | Convert encrypted data to its original form so it can be understood by both users and systems. This can be used to find protected and hidden files, detect deleted data, and recover complex passwords during forensic investigations. |
Keyword search | Find specific evidence within a large collection of data. Users can add multiple keywords at once to search digital documents and attachments. |
Timeline analysis | Collect and analyze chronological event data to determine what occurred and when within a filesystem for forensic purposes. This can help answer questions about when a computer/device was used or what occurred before/after a security incident. |
What type of buyer are you?
Understanding the different types of digital forensics software buyers in the market will help you determine what type of buyer you are and make an informed purchase. The majority of digital forensics software buyers fall into the following categories:
Legal enforcement agencies: These agencies use computers and software to fight crimes in both criminal and civil cases, as well as present evidence in court. These buyers should look for solutions that can help them in cases concerning mishandling of government data, identity theft, privacy concerns, and sexual harassment. A multipurpose digital forensics tool that offers electronic discovery, memory forensics, cyberforensics, and remote forensic capabilities would be a good fit for these buyers.
Commercial organizations: These organizations often deal with insider threats, cyberthreats, or data loss, which can be costly. Using digital forensics software to gather information from company devices can be more cost-effective than hiring a dedicated investigative team. These orgs should consider digital forensics tools with features including network monitoring and data/file recovery to aid in instances of intellectual property theft, employment disputes, bankruptcy investigations, and fraud compliance.
Benefits of digital forensics software
Let’s take a look at some of the benefits of using a digital forensics tool:
Ensure system integrity: These tools manage vast volumes of digital evidence without altering the data within a system. This means users can document who accessed the system, when, and from where to maintain system integrity and determine whether it was subject to any criminal activity or policy violations.
Recover stolen/deleted information: In a business data breach or case of stolen identity, recovering stolen or deleted information is crucial. Digital forensics software can help users recover stolen or deleted files, passwords, and other data that was erased or damaged.
Prevent hackers and viruses: Data collected with a digital forensics tool can impact future cybersecurity. The trends identified from collected data can help users learn how a virus was introduced to a device or network, or how hackers accessed, stole, deleted, and exploited information. Such data can help companies to prevent cyberthreats, detect relevant data to protect, and pay special attention to emails and files that they receive.
Market trends to understand
Here’s a digital forensics software market trend to keep in mind when making your purchase:
Increasing role of artificial intelligence (AI) in digital forensics software. Digital forensics investigators are exposed to ever increasing amounts of data from social media, the cloud, personal networks, smart sensors, and video footage. AI technology has improved investigators' ability to identify and investigate the root cause of cybercrimes. Digital forensics software paired with AI technology offers intelligent analysis of unstructured data to identify potential suspects or predict where cybercrime is likely to occur. In the future, software providers may use AI to facilitate collaborative analysis of cybercrime and recognize patterns in programmatic signatures of suspected criminals.
Note: The application selected in this article is an example to show a feature in context and is not intended as an endorsement or recommendation. It has been obtained from sources believed to be reliable at the time of publication.







