How to Avoid the Worst Manufacturing Cyber Security Risks
The digital transformation in manufacturing promises a slew of incredible boosts to your operational visibility and production efficiency. In turn, companies are adopting and integrating new hardware and software at a rapid pace to experience these benefits.
The problem? Due to the speed and volume of these implementations, businesses are unknowingly peppering their production systems with cybersecurity gaps.
Perhaps the most obvious approach would be to patch these holes to prevent intrusions, but Gartner strongly recommends a different method (full content available to clients):
If manufacturers switch focus from prevention to a detect and response approach for cybersecurity risks, they are twice as likely to eliminate threats of IP theft and avoid disruptions that can cost an average of $300,000.
Keep reading for a rundown of the ways hackers can get into your system, a few easy steps that make their attack more difficult and expert advice to keep them out in the first place.
Prevention Won’t Work—Detect and Respond to Cyber Threats
Much of a manufacturer’s value is in how they create their products—sensitive intellectual property, trade secrets that set them apart—and thanks to the rise of cloud technology, most of it is online. Kaspersky shows this information is already at risk:
Number of Cyber Security Attacks in 2017 (Per Affected Industrial Company)

(Source)
At this point, the experts agree that preventing these attacks isn’t working, says Chris Morales, head of security analytics at Vectra Networks, which provides AI-powered cybersecurity platforms for various industries, including many manufacturing clients.
“Not only do manufacturers have all these devices, they’ve also adopted a whole cloud architecture where they’re taking all their data and sending it out,” he says. He goes on to point out that “they have a very large attack surface.”
It’s no surprise that Gartner predicts that this will result in nearly eventual downtime:
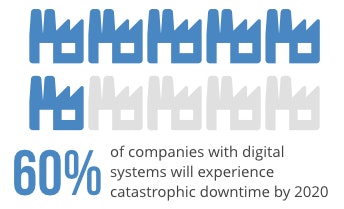
(Source—full content available to clients)
This large attack surface also means malicious viruses can go unnoticed on one of the several devices or computers. Research shows that the beginning of the attack and when a company notices it are often dangerously far apart.
“One of the most common misnomers or misunderstandings that we encounter is that cyberattacks happen in seconds, but the reality is they transpire over days and sometimes weeks,” says Mike Banic, Marketing VP at Vectra.
So detection speed is the important factor that can most greatly reduce the impact of an attack to steal trade secrets or disrupt your operations. Morales describes three key hacker network behaviors they look for:
Remote access allows attackers to influence your physical systems from a distant location and create a botnet (a group of networked devices infected with malicious software controlled by the hacker).
Automated replication is the process of malware or a virus to create copies of itself on more computers in the network.
Exfiltration refers to hackers sending your operational data out to unauthorized places instead of the cloud or server you established.
“[Attackers are] trying to blend in, and it’s the security team’s goal to be able to look at these detections and determine if it’s approved or unapproved,” Banic says. “For the ones that are approved, they can actually teach the AI brain—they can tell the brain this is actually approved behavior and the brain won’t alert them on it.”
Case-in-Point: TSMC Loses Millions in Malware Attack
Morales and Banic point to a recent case—Taiwan Semiconductor Manufacturing Company (TSMC) is the world’s largest semiconductor producer, and the top supplier for Apple mobile devices. On August 3, employees connected a new manufacturing software tool to the TSMC network.
Coming in a nontraditional way, the software had already been infected with a version of the WannaCry ransomware, which replicated itself onto several other computers, equipment and materials systems and caused three days of downtime.
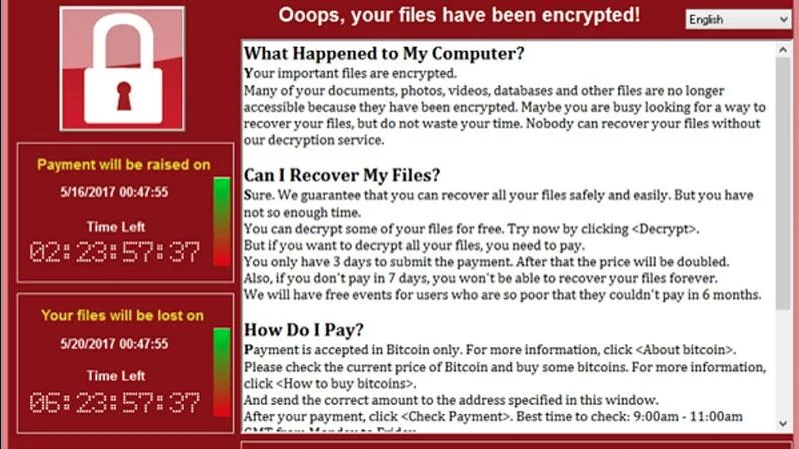
Screen capture of the WannaCry malware (Source)
The incident cost the company delays, extra costs and a loss of nearly $200 million in revenue. Banic says this illustrates the idea that prevention can’t cover all the possible attack locations, whereas a detect and response approach could have spotted the intruder earlier.
“Prevention is based on the idea that I’m going to stop an outsider attack getting in,” he says. “What happens when it’s your technicians installing software and the software was bad to begin with?”
4 Ways to Enable Detection and Response
Adopting network security software with detect and respond capabilities is your best bet. Smaller manufacturers may only have a single person managing IT security, and AI-powered network detection can give them what feels like an intelligent partner that can spot intrusions much more quickly.
Vectra’s Cognito leverages user and entity behavior analytics (UEBA) to detect intrusions that bypassed firewalls or other controls, then packages alerts together for a simpler investigation.
“[AI] augments human talent so that you don’t need a massive staff,” Morales says. “You can actually combine a person with AI, and you’re able to watch every device in real time, and combined, they make the decision on how to respond.”
Even if you’re only evaluating manufacturing security solutions now, Morales outlines a few actions manufacturers can take to create a more secure digital environment:
Establish network visibility, not just into what attackers may be doing, but the status of your production lines, manufacturing and the supply chain. “In order to find something wrong or respond to it you actually have to know even what’s going right,” Morales says.
Map out your attack surface so you know the exact devices or connections that leave your company exposed. Especially for companies that have implemented internet of things devices and/or networked assets. Think of each asset like valuables in your home.
“You want to be able to protect it so you should know who has access to the room where it’s stored and the cabinet that it’s in,” Morales says. “and it is very much the same conversation in a manufacturing environment: What are your key assets? How can they be accessed?”
Prioritize critical assets to establish a hierarchy during attacks. For example, manufacturers can bulk upload these critical machines into the detection software, and any attack that affects those assets will have a higher priority. Morales says the system will be alerted if malware tries to perform reconnaissance on a critical asset.
Eliminate bad practices related to human error. As mentioned above, Morales recommends consistently checking where your data is going. If you’re using Microsoft Azure to store your production data, ensure hackers aren’t redirecting that traffic to a different cloud in a different country. Also, carefully inspect external solutions for malware before integrating them with the rest of your network.
How Can I Learn More About Manufacturing Security?
Gartner recommends applying a mix of prevention and detect and response capabilities to best prevent or eliminate cybersecurity threats. We have a few resources to help you move forward:
Find more research that compares ERPs with MRPs and best practices for outsourcing safely.
Read real user reviews for a wide variety of manufacturing and security systems.
If you prefer some help, call our expert advisors at (855) 998-8505 for a free consultation. In about 10 minutes, they can narrow down your best options that meet your particular needs.