Find the best Multi-Factor Authentication Software
Compare Products
Showing 1 - 20 of 84 products
Sort by
Reviews: Sorts listings by the number of user reviews we have published, greatest to least.
Sponsored: Sorts listings by software vendors running active bidding campaigns, from the highest to lowest bid. Vendors who have paid for placement have a ‘Visit Website’ button, whereas unpaid vendors have a ‘Learn More’ button.
Avg Rating: Sorts listings by overall star rating based on user reviews, highest to lowest.
A to Z: Sorts listings by product name from A to Z.
ManageEngine ADSelfService Plus
ManageEngine ADSelfService Plus
ADSelfService Plus is an identity security solution that ensures secure and seamless access to enterprise resources and establishes a Zero Trust environment. With adaptive multi-factor authentication (MFA), single sign-on (SSO), s...Read more about ManageEngine ADSelfService Plus
NordPass Business
NordPass Business
NordPass Business — The Ultimate Password Manager for Your Organization. Trusted by businesses worldwide, NordPass Business offers a cutting-edge, zero-knowledge security architecture password management solution for businesses o...Read more about NordPass Business
Twilio User Authentication & Identity
Twilio User Authentication & Identity
Twilio User Authentication & Identity offers digital identity verification and intelligence tools to build mutual trust between business and consumer. Verify end-users are who they say they are across SMS, email, WhatsApp, TOTP, ...Read more about Twilio User Authentication & Identity
Ping Identity
Ping Identity
At Ping Identity, we believe in making digital experiences both secure and seamless for all users, without compromise. We call this digital freedom. And it's not just something we provide our customers. It's something that inspire...Read more about Ping Identity
OneLogin
OneLogin
OneLogin is a cloud-based identity and access management solution that helps users control access to facilities, web applications, data centers, cloud storage and more. Key features include single sign-on, web access management, a...Read more about OneLogin
Auth0
Auth0
Auth0, a product unit within Okta, takes a modern approach to identity, enabling organizations to provide secure access to any application, for any user. The Auth0 Identity Platform is highly customizable, as simple as development...Read more about Auth0
SecureAuth
SecureAuth
SecureAuth is a cloud-based software that helps businesses manage and verify user identities through various authentication tools, such as MFA, password-less authentication and more. Professionals can use the dashboard to monitor ...Read more about SecureAuth
Trusona
Trusona
Trusona is a leader of passwordless MFA solutions for enterprises within the financial services, healthcare, higher education, media industry. The company's workforce solutions provide a complete authentication alternative to user...Read more about Trusona
DigitalPersona
DigitalPersona
DigitalPersona is an identity management software, which helps businesses in finance, healthcare, government and other sectors with multi-factor authentication to protect data. The solution provides a single sign-on (SSO) portal, ...Read more about DigitalPersona
Passportal
Passportal
N-able Passportal is a cloud-based solution, which helps small to large managed service providers (MSPs) automate password protection and organize relative documents. Key features include credential injection, password change mana...Read more about Passportal
Imprivata Privileged Access Management
Imprivata Privileged Access Management
Xton Access Manager is an identity management solution that caters to businesses across various industries. Key features include access request management, role management, compliance management, single sign-on and user provisioni...Read more about Imprivata Privileged Access Management
swIDch Auth SDK
swIDch Auth SDK
swIDch Auth SDK provides multiple robust authentication features such as FIDO-certified biometric authentication, mOTP authentication for easy mobile application, and the world’s first one-way dynamic code OTAC login. swIDch Aut...Read more about swIDch Auth SDK
LastPass
LastPass
LastPass is a password management solution for consumers and businesses that allows users to store their passwords in a digital vault. It uses single sign-on with password vaulting to protect users’ passwords. Users can save the w...Read more about LastPass
ZenKey
ZenKey
ZenKey is a web-based identity management solution designed to help businesses streamline authentication and identity validation. Key features include face recognition, fraud detection, biometrics, and multifactor authentication. ...Read more about ZenKey
2FA for Jira: U2F & TOTP
2FA for Jira: U2F & TOTP
The proven enterprise-grade solution for the secure two-factor authentication for Jira with TOTP and U2F support. The plugin allows users to select a relevant second authentication factor (TOTP, Webauthn/biometrics or U2F device) ...Read more about 2FA for Jira: U2F & TOTP
UserLock
UserLock
UserLock provides Multi-Factor Authentication and Access Management on Active Directory user accounts. Verify the identity of all users and secure access to Windows Logins, RDP, RD Gateway, VPN, IIS, and Cloud Applications. User...Read more about UserLock
2FA for Confluence: U2F &TOTP
2FA for Confluence: U2F &TOTP
2FA for Confluence: U2F & TOTP is an app used by IT security admins to add an extra level of protection for Confluence users during sign-in. It features passwordless authentication options, login via backup code list, IP address a...Read more about 2FA for Confluence: U2F &TOTP
Armour365
Armour365
armour365 is a language-independent Ai-powered voice biometrics software. armour365 keenly notes the user’s accent, vocal cord & nasal passage movement while speaking, and 140+ other key elements to create a unique voiceprint. A...Read more about Armour365
Entrust Identity as a Service
Entrust Identity as a Service
Entrust Identity as a Service is a cloud-based identity and access management service that provides digital security solutions for banking, government, healthcare and enterprise organizations globally. This solution streamlines id...Read more about Entrust Identity as a Service
ID.me
ID.me
ID.me is a digital identity network where individuals verify their identity once, and never have to re-verify their identity again across any organization where ID.me is accepted. It’s just like the driver's license in the physica...Read more about ID.me
Popular Comparisons
Buyers Guide
Last Updated: March 16, 2023Multi-factor authentication (MFA) software is essential for businesses to secure sensitive data. Whether it’s bank accounts, work accounts, applications, or cloud storage, instituting multi-factor authentication will ensure that only you or other authorized users have access to accounts that are critical to your business, which will protect you from data breaches.
In addition, the software offers features such as threat detection, incident response, remote access, endpoint monitoring, and more, making it a complete security solution.
Before you buy the software, you need to understand what multi-factor authentication software is, its features, who typically buys this type of software, and the benefits it will bring to your business. This buyers guide also covers some key considerations before purchasing software and the latest technology trends in the market.
Here's what we'll cover:
What is multi-factor authentication software?
Multi-factor authentication software is a cloud-based tool that helps businesses manage accounts carrying sensitive information via meta-directory, one-tap access, single sign-on, and more.
The software secures the accounts by prompting the owner or stakeholders to prove their identity through a set authentication method. This could be a one-time password (OTP), security key, hardware tokens, app-generated code, a mobile push message, or a phone call to the registered number. Once the user’s identity is proven, the user can access accounts, applications, and systems critical to the business, all in one go.
Multi-factor authentication software is used by businesses in hospitality, finance, healthcare, law, and ecommerce. However, businesses catering to other sectors along with entrepreneurs and individuals can also leverage this technology to enhance data security.
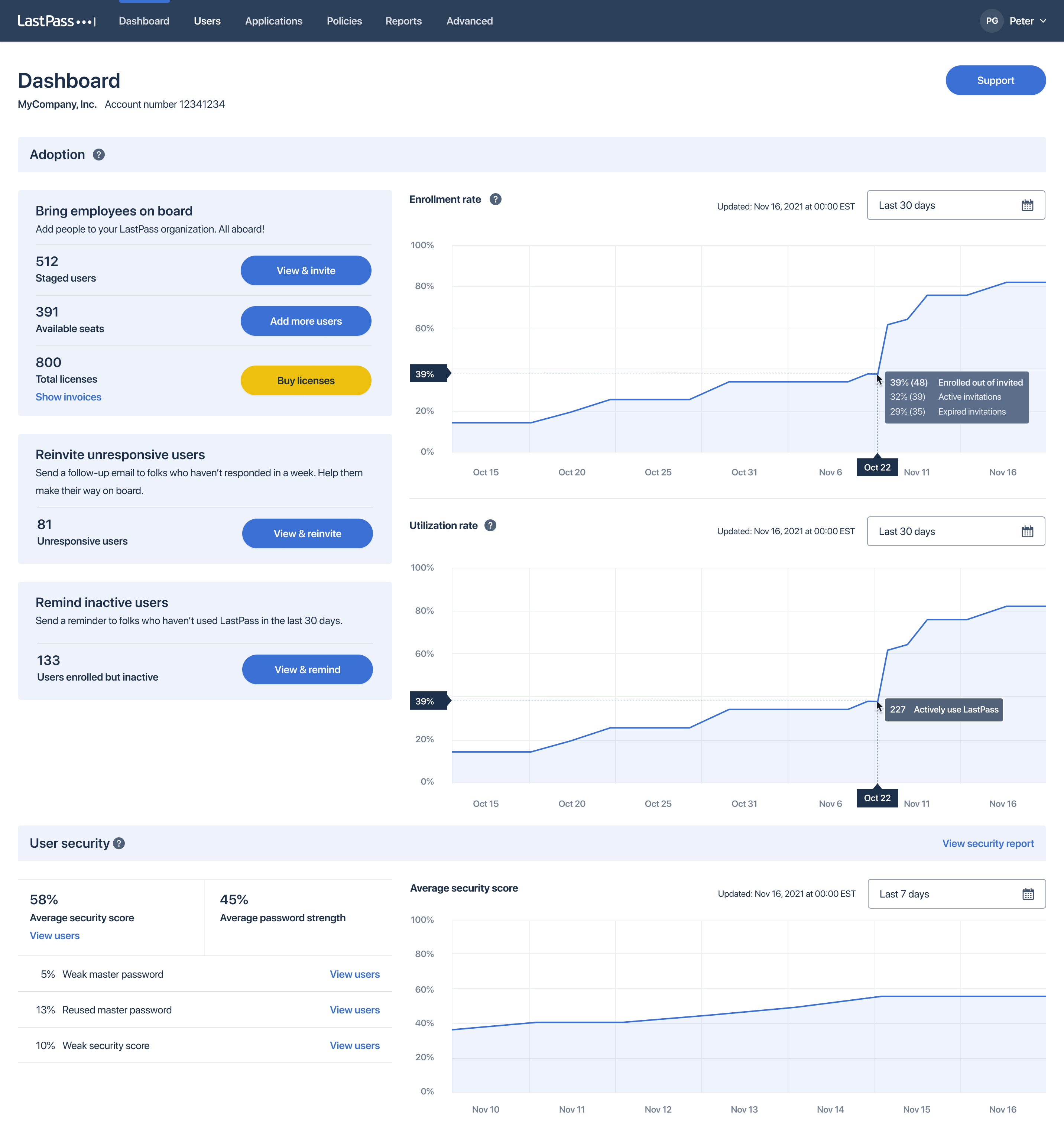
Dashboard in LastPass (Source)
Common features of multi-factor authentication software
Control who can have access to the accounts that are registered for multi-factor authentication. You can also define user groups and access policies to enhance security. | |
Credential management | Store usernames and passwords for multiple accounts in one place. Utilize them when facing issues during login and delete or change the information when you are alerted about unauthorized access. |
Get fast and secure access to single or multiple accounts by approving a push notification for login on your mobile device. | |
Multiple authentication methods | Select from multiple authentication options such as tapping on a universal 2nd factor (U2F) USB device, approving a push notification, entering an OTP, using biometrics, and more. |
Self-service portal | Save time for both you and your administrator by utilizing the self-service feature to add or change credentials, manage accounts, set up threat alerts, and more. |
Single sign-on (SSO) | Experience a consistent and hassle-free login experience for single or multiple accounts, whether from the office or a different location via your mobile device. |
What type of buyer are you?
Financial businesses: Financial service providers are prime targets of cyber theft. That makes it essential to have a fool-proof multi-factor authentication method in place to ensure data security and protect against breaches.
Such businesses can utilize multi-factor authentication software to secure applications, systems, and networks and can also pick different authentication methods to manage internal and external identities.
Legal firms: It is the ethical duty of a legal firm to protect their clients’ data, so they require multi-factor authentication software. The software can help mitigate the threat to the information infrastructure of these businesses by requesting unique identification information, in addition to a user’s username and password. These businesses can leverage the access management feature of the software to allow authorized access to clients and other stakeholders using a security key.
Healthcare businesses: Healthcare businesses require strong access control to help mitigate security risks related to remote access to patients’ data. Utilizing a fully-featured multi-factor authentication software with access management can help keep data secure. In addition, patients can also leverage the self-service portal to get secure access to the information they need.
Consumer businesses: Data security is essential in the consumer business, both for customers and owners. While customers fear identity theft and misuse of payment options, it is also not pleasant for business owners to fall prey to false payments made by digital thieves. Employing a multi-factor authentication software with a self-service feature will strengthen the security for these businesses, ensuring a hassle-free customer experience.
Corporate enterprises: In the digital workspace, information critical to a business is accessed by partners, employees, and vendors from a multitude of locations and networks. This brings along the risk of security breaches, but a multi-factor authentication software can help mitigate the risk. Not only does it help in user identity verification by gaining visibility into devices, but it also enforces adaptive policies to secure access.
Benefits of multi-factor authentication software
Reduces security breaches: Multi-factor authentication software offers endpoint security and visibility into all the end user devices that have access to sensitive data. This ensures strong authentication and prevents security breaches.
Improves access management: A strong MFA solution combined with convenient features such as a self-service portal or one-tap biometric authentication helps stakeholders to access the information quickly.
Enhance operational efficiency: Notifying stakeholders of each login attempt involves time and effort. However, the authentication software with features such as push notifications can reduce help desk efforts, which will allow them to focus on other essential aspects of the business.
Key considerations when purchasing multi-factor authentication software
Business needs: Every business has different compliance and security policies, depending on the nature of their work. This makes it essential to look for an adaptive MFA software that can align with your business requirements, such as cloud applications, remote access, a self-service portal, and more.
Budget: Price is an important factor when talking about long-term investments, especially in the case of small businesses. This makes it essential to look at the software subscription plans that can be included in the present operational cost of the business.
Market trend to understand
Here is a multi-factor authentication software market trend that you need to be aware of:
AR to soon redefine user authentication: Augmented reality (AR) and virtual reality (VR) have shown promising results in various industries, and now there are plans to use the technology to enhance multi-factor authentication. With the technology in place, an AR interactive system will initiate a conversation with the user to conduct identity tests via questions and images. While the basic principle of authentication remains the same, the AR interactive system will take the place of a textual authentication format. This innovation is currently being tested for its effectiveness, with plans to be launched in the near future.
Note: The application mentioned in this guide is an example to show a feature in context and is not intended as an endorsement or recommendation. It has been taken from sources believed to be reliable at the time of publication.







