Find the best Customer Identity and Access Management (CIAM) Software
Compare Products
Showing 1 - 20 of 65 products
Sort by
Reviews: Sorts listings by the number of user reviews we have published, greatest to least.
Sponsored: Sorts listings by software vendors running active bidding campaigns, from the highest to lowest bid. Vendors who have paid for placement have a ‘Visit Website’ button, whereas unpaid vendors have a ‘Learn More’ button.
Avg Rating: Sorts listings by overall star rating based on user reviews, highest to lowest.
A to Z: Sorts listings by product name from A to Z.
Twilio User Authentication & Identity
Twilio User Authentication & Identity
Twilio User Authentication & Identity offers digital identity verification and intelligence tools to build mutual trust between business and consumer. Verify end-users are who they say they are across SMS, email, WhatsApp, TOTP, ...Read more about Twilio User Authentication & Identity
Auth0
Auth0
Auth0, a product unit within Okta, takes a modern approach to identity, enabling organizations to provide secure access to any application, for any user. The Auth0 Identity Platform is highly customizable, as simple as development...Read more about Auth0
OneLogin
OneLogin
OneLogin is a cloud-based identity and access management solution that helps users control access to facilities, web applications, data centers, cloud storage and more. Key features include single sign-on, web access management, a...Read more about OneLogin
FusionAuth
FusionAuth
FusionAuth is a customer identity and access management (CIAM) software designed to help developers authenticate, authorize and manage user access. The platform enables administrators to assign roles to team members and secure log...Read more about FusionAuth
Omada Identity
Omada Identity
Omada, a market leader in modern Identity Governance & Administration (IGA), provides the most comprehensive IGA as a Service solution on the market today to help organizations enable and secure all their identities. Omada Identit...Read more about Omada Identity
CoreOne Suite
CoreOne Suite
CoreOne Suite is a cloud-based and on-premise identity and access management(IAM) solution that provides solutions for Enterprise IAM, Customer IAM and Single-Sign On(SSO). Depending on the industry or business, CoreOne identity p...Read more about CoreOne Suite
Ping Identity
Ping Identity
At Ping Identity, we believe in making digital experiences both secure and seamless for all users, without compromise. We call this digital freedom. And it's not just something we provide our customers. It's something that inspire...Read more about Ping Identity
AU10TIX
AU10TIX
AU10TIX is a cloud-based identity management solution that helps organizations in financial services, marketplaces, telecommunication, and other verticals handle identity verification processes. The software assists businesses wit...Read more about AU10TIX
LoginRadius
LoginRadius
LoginRadius is a cloud-based customer identity and access management solution for businesses in industries such as media, publishing, travel, nonprofit, e-commerce and sports. Key features include customer registration and authent...Read more about LoginRadius
RapidIdentity
RapidIdentity
RapidIdentity is an identity and access management platform that provides features such as automated lifecycle management, identity governance, multi-factor authentication and password management. The solution provides role-based ...Read more about RapidIdentity
System Frontier
System Frontier
System Frontier is an identity management solution that caters to businesses in various industries such as financial services, energy and utilities, education, health care and more. Key features include access request management, ...Read more about System Frontier
Prove ID
Prove ID
Prove ID is an end-to-end ID verification & management tool for online businesses. It enables remote parties to authenticate each other with a customizable verification process. The platform brings a performance-based approach to ...Read more about Prove ID
walt.id Identity Infrastructure
walt.id Identity Infrastructure
We offer holistic digital identity and wallet infrastructure used by thousands of developers, governments and businesses across industries. The products are open source, based on open standards, compliant with digital identity r...Read more about walt.id Identity Infrastructure
strongDM
strongDM
strongDM is a database management software tool designed for SMBs and agencies. It aims to provide technical staff, including CTOs, CIOs, DevOps, and infrastructure engineers, secure access to their company's resources. It blends ...Read more about strongDM
SAP Customer Data Cloud
SAP Customer Data Cloud
SAP Customer Data Cloud enhances customer experiences across marketing, commerce, sales, and service. Unify all customer data sources, respect data privacy, and activate rich insights in real time to exceed customer expectations a...Read more about SAP Customer Data Cloud
Oz Liveness
Oz Liveness
Oz Liveness is a facial recognition and authentication software designed to help private and public organizations across the globe lower biometric fraud risk by preventing deep fake and spoofing attacks. Organisations can successf...Read more about Oz Liveness
Frontegg
Frontegg
A user management platform available only in English, Frontegg was built for B2B, B2C, and SaaS product developers who use the product-led growth (PLG) methodology. Users embed 5 lines of code in their app to deploy a user managem...Read more about Frontegg
miniOrange
miniOrange
The simplest platform which integrates thousands of applications with convenient features such as SSO, MFA, Provisioning, etc. with any user source - AD, Azure AD, Okta, miniOrange. The product offers comprehensive features such ...Read more about miniOrange
Sumsub
Sumsub
Sumsub is an all-in-one technical and legal toolkit for KYC/AML needs. The company provides a web-based platform for converting customers, speeding up verification, reducing costs and detecting digital fraud. Sumsub’s global clien...Read more about Sumsub
Authfy
Authfy
Authfy is a SEC4U low-code platform, a company focused on Cyber Identity, which enables secure digital journeys, providing the best experience for customers: frictionless and passwordless, unifying the entire authentication path ,...Read more about Authfy
Popular Comparisons
Buyers Guide
Last Updated: March 16, 2023Software Applications for Customer Identity and Access Management (CIAM)
Over the past few years, there’s been a major shift in the way customers interact with brands. The importance of customer identity and access management (CIAM) is growing as stolen passwords and data breaches are becoming a more and more common threat.
CIAM tools add an additional layer of security over your business network, making it harder for outsiders to steal critical information.
With this in mind, we created this CIAM software buyers guide to help you better understand how this software works, identify some common features to look for, and make the right choice for your organization.
Here’s what we’ll cover:
What is customer identity and access management (CIAM) software?
Common features of customer identity and access management (CIAM) software
Benefits of customer identity and access management (CIAM) software
What is customer identity and access management (CIAM) software?
CIAM solutions help companies securely manage and safeguard customer identities and access across business units.
The main purpose of CIAM software is to manage customer information and provide self-service customer registration, access management, single sign-on (SSO), and multifactor authentication (MFA) across digital channels, including mobile devices, the web, apps, etc.
Usually, CIAM software does three major things:
Minimizes the risk of account takeover while improving customer login and customer registration experiences.
Provides customized experiences such as customer access to a secure login portal with an authentication requirement.
Offers scalable solutions to support a number of customers.
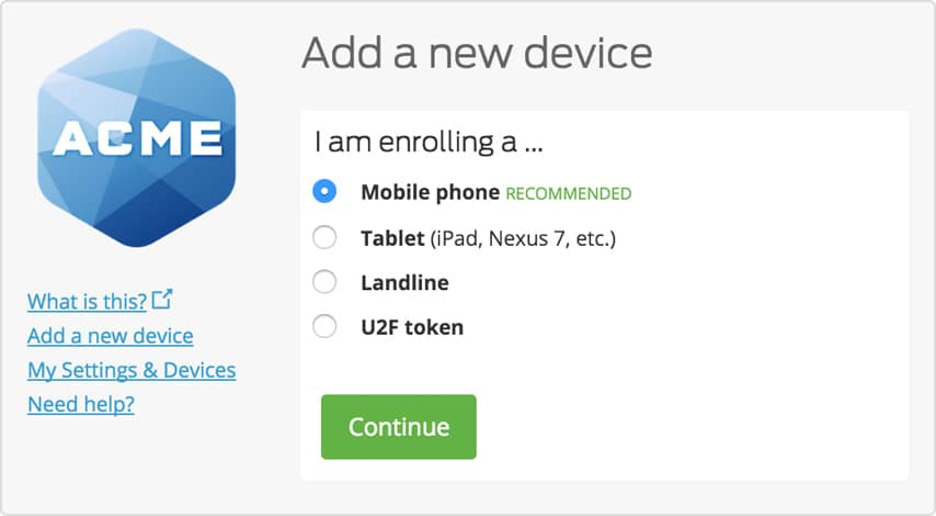
Multifactor authentication in Duo Security (Source)
Common features of CIAM software
Access management | Control who can access accounts registered for multifactor authentication. Define user groups and access policies to enhance security. |
Multiple authentication methods | Select from multiple authentication options such as using a universal 2nd factor (U2F) USB device, approving a push notification, entering an OTP, using biometrics, etc. |
Access certification | Verify user access rights within systems to confirm each user has appropriate and authorized access to resources. |
Behavioral analytics | Track and analyze user behavior within a system or network. |
Credential management | Store usernames and passwords for multiple accounts in one place. |
Multifactor authentication | Use multiple, independent data components from a user to verify identity before they can gain access to the system. Typically, this requires a user to both enter their password as well as an encrypted, randomly generated code created on demand. |
Reporting/Analytics | View and track pertinent metrics. |
Self-service portal | Save time by enabling a self-service feature to add or change credentials, manage accounts, set up threat alerts, and more. |
Notifications | Informational updates that are delivered to users as soon as an event occurs. |
What type of buyer are you?
Most CIAM software buyers belong to one of the following categories:
Law firms: These buyers include legal professionals that need to protect client identities and information. CIAM software can help firms avoid threats to their information infrastructure by requiring unique identification information to access data. These firms can leverage CIAM software's access management features to provide authorized access to clients and other stakeholders using security keys.
Consumer businesses: When it comes to consumer businesses such as ecommerce platforms, data security is important for both customers and owners. With multiple authentication methods to gain access to a profile/account, CIAM software helps consumer-facing businesses give customers extra levels of protection.
Corporate enterprises: Critical information and data is routinely accessed by partners, employees, and vendors from a multitude of locations and networks in the modern digital workspace. This brings a risk of security breaches, which CIAM software can help mitigate. Not only does it help verify user identity by gaining visibility into the devices that are accessing information, it also enforces adaptive policies to secure access by requiring certain user credentials.
Benefits of customer identity and access management (CIAM) software
Reduced security breaches: CIAM software offers several security features such as risk-based authentication to secure customer details across the consumer lifecycle while supporting security policies. For example, each customer’s login patterns are tracked to identify any unusual activity. The tool offers multiple forms of identity authentication to help prevent security breaches.
Improved access management: A CIAM solution that offers features such as a self-service portal and MFA helps stakeholders access the information they need, quickly.
Improved user experience: Many companies have multiple web applications and portals, requiring users to authenticate their login multiple times when switching between applications. By integrating all digital channels and applications with a single CIAM solution, you can provide a more seamless user experience: one point of entry for all applications.
Key considerations when buying CIAM software
Does the software allow social login? If you want to authenticate customer identity, look for a solution that allows users to create an account or sign in using existing social accounts on websites such as Facebook or Google. This can help you streamline the user experience with both registration and ongoing authentication.
Does the solution support multifactor authentication? If you want to make sure your system is secure, look for CIAM tools with multifactor authentication that requires users to have both their password and access to a backup form of identification (such as a separate email address or phone number where an access code can be sent).
Budget: Price is an important factor when talking about long-term investments, especially for small businesses. It's important to look at the pricing plans offered by software vendors to ensure you don't exceed your budget.
Note: The application shown in this article is an example to show a feature in context and is not intended as endorsements or recommendations. It was obtained from sources believed to be reliable at the time of publication.