How to Protect Your ERP Data With Access Control
There are some risks you just shouldn’t take—especially when it comes to data security.
As the home to all your most vital business information, ERP software, of all things, should be a risk-free zone. Unauthorized users are prone to misuse of sensitive data, whether intentional or unintentional, presenting a significant security liability to businesses of all sizes.
One of the best ways to mitigate risk in an ERP is through access control, ofter referred to as identity and access management (IAM), defined by Gartner as “the security discipline that enables the right individuals to access the right resources at the right times for the right reasons.”
In other words:
 To reduce the risk of security breaches and safeguard sensitive data, businesses must thoroughly vet users and restrict ERP access to a strict need-to-know basis.
To reduce the risk of security breaches and safeguard sensitive data, businesses must thoroughly vet users and restrict ERP access to a strict need-to-know basis.
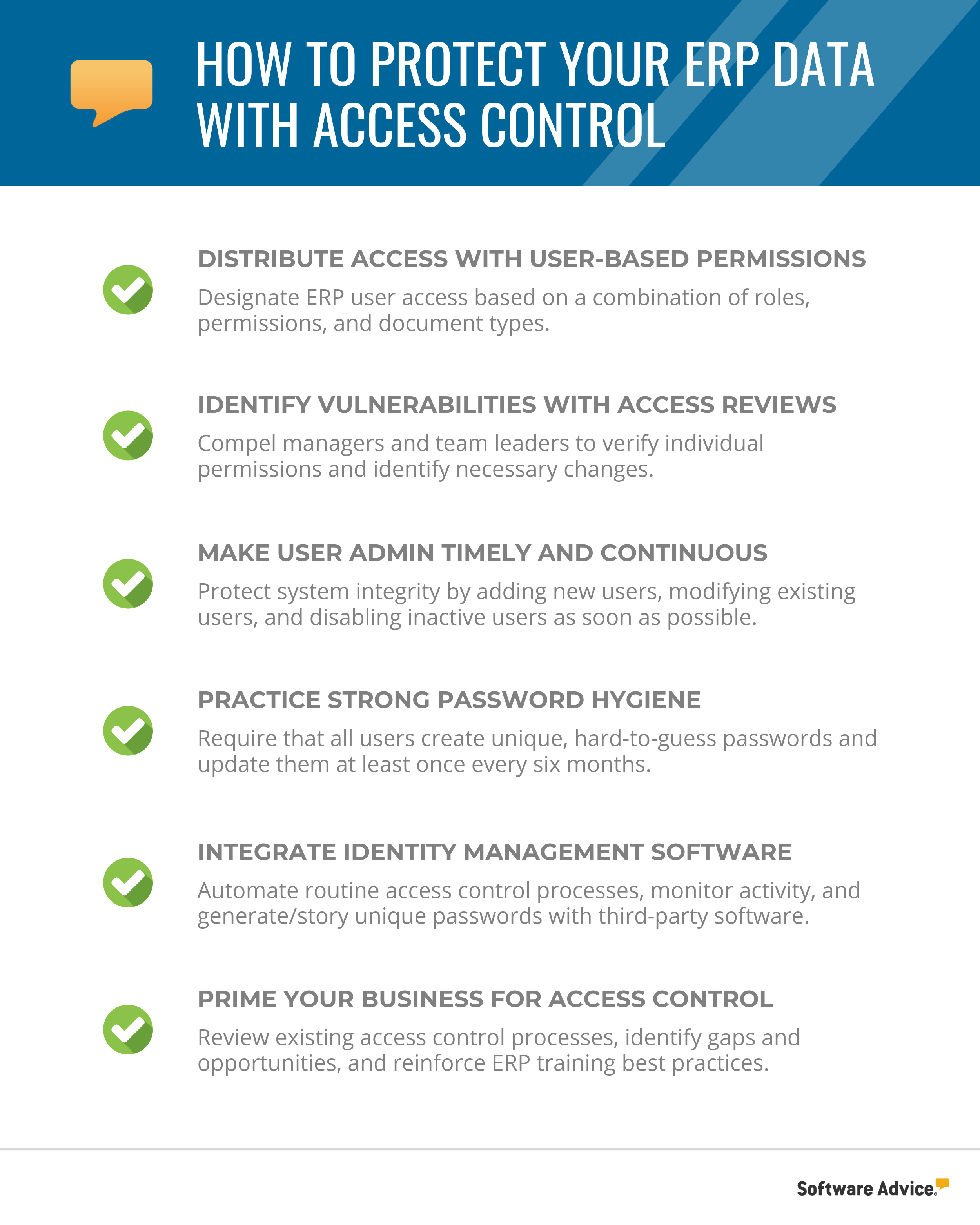
As we’ll explain in this article, ERP access control entails the strategic application of the following best practices:
Let’s take a closer look at each of these strategies.
Distribute access levels with user-based permissions
Just as you wouldn’t hand the keys to a Ferrari to an unruly teenager, never grant high-level admin or configuration rights to anyone who hasn’t earned them. Instead, only permit the necessary level of access required to do a job—no more, no less.
ERP access should be distributed according to some combination of the following:
User role. Different roles come with different responsibilities, and Jeff in accounting shouldn’t have free rein over your supply chain management component. Designate the necessary ERP access for every role within your organization, down to the individual component, then assign those roles to each user in the system.
Permission level. Senior- and management-level employees typically have more experience—in both the company and the system—and their permissions should reflect that. Assign a permission level to each role, usually in the form of a number (0, 1, 2, 3)—the higher the number, the more access is granted.
Document type. Not all documents are created equal. For instance, an entry-level sales representative might need access to a sales invoice, but not the underlying contract. Protect your high-level documents by assigning them a higher privilege or permission level.
Identify vulnerabilities through periodic access control reviews
Between all the inevitable organizational changes and workflow refinements, the roles and responsibilities of your ERP users can change at a moment’s notice. That’s why it’s always a good idea to schedule regular ERP access control reviews—and make sure everything looks as it should.
The best way to go about this is to segment reviews by department, requiring managers and team leaders to verify individual permissions and identify necessary changes.
Advise your managers to look for the following warning signs:
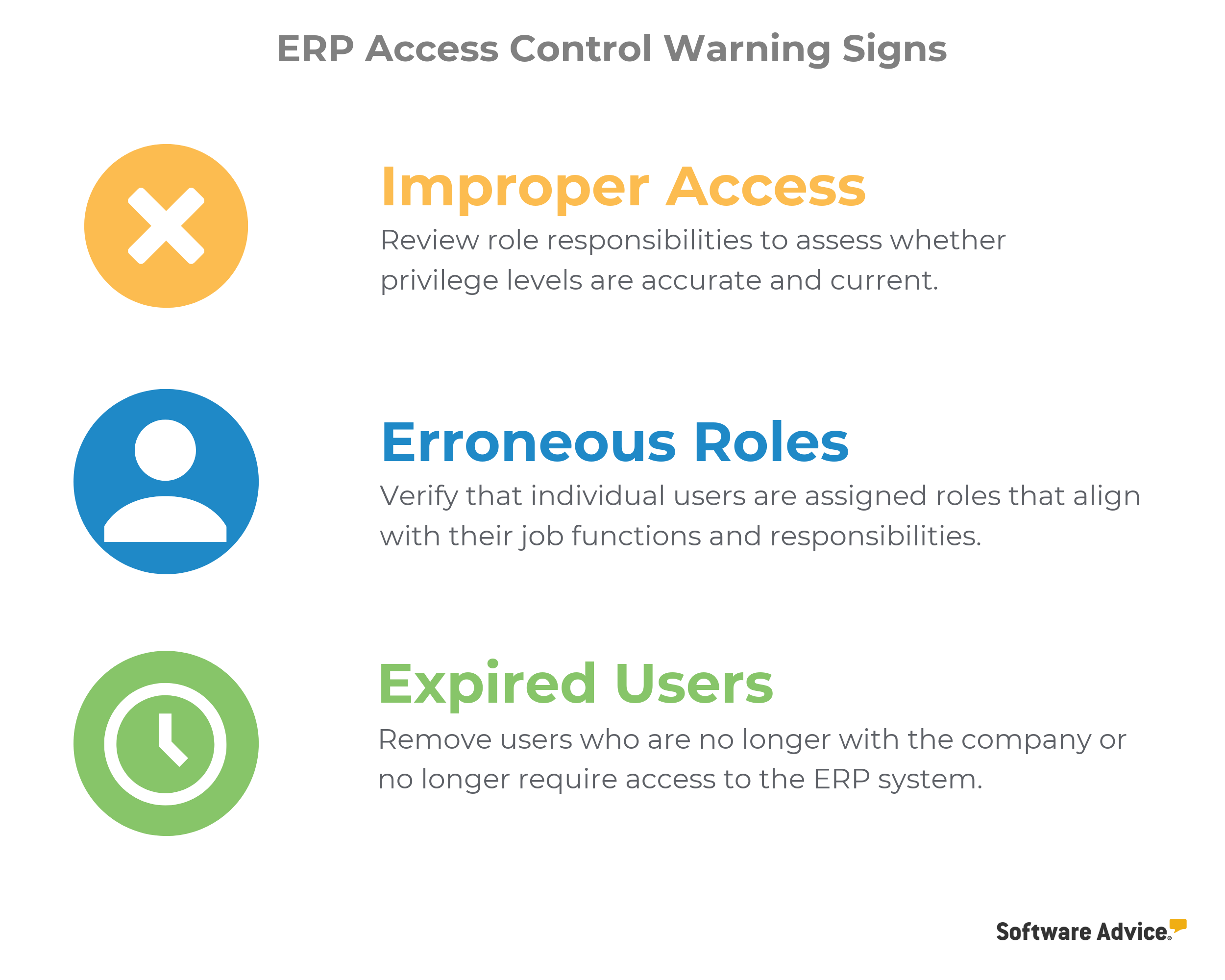
Be sure to keep a regular audit trail of ERP access control reviews, which can help keep your business compliant with industry regulations such as the Sarbanes-Oxley Act (SOX).
Verify that user administration is continuous and immediate
In addition to regular audits, user administration should be ongoing, with strict guidelines and process standards to ensure that role changes are reflected in the system instantaneously.
This process includes:
Adding new users. Before adding new users or hires to the system, request that their manager provide a detailed list of modules required to perform their duties.
Modifying existing users. If the responsibilities of an existing user change, or if the user requests access to a previously gated module, consult their manager to determine which permissions should be granted.
Disabling inactive users. This is one of the most important safeguards against unauthorized access. Regardless of how trustworthy an ex-employee was, if their account remains active in the system, your ERP data is subject to security breaches.
Ideally, all changes should be made as soon as a new employee is hired, an existing employee is reassigned, or a former employee leaves the company. The longer you wait to make necessary adjustments, the more vulnerable your ERP data becomes.
Require strong passwords and update logins regularly
In this ever-evolving era of cybersecurity threats, your ERP’s security begins at the individual user level.
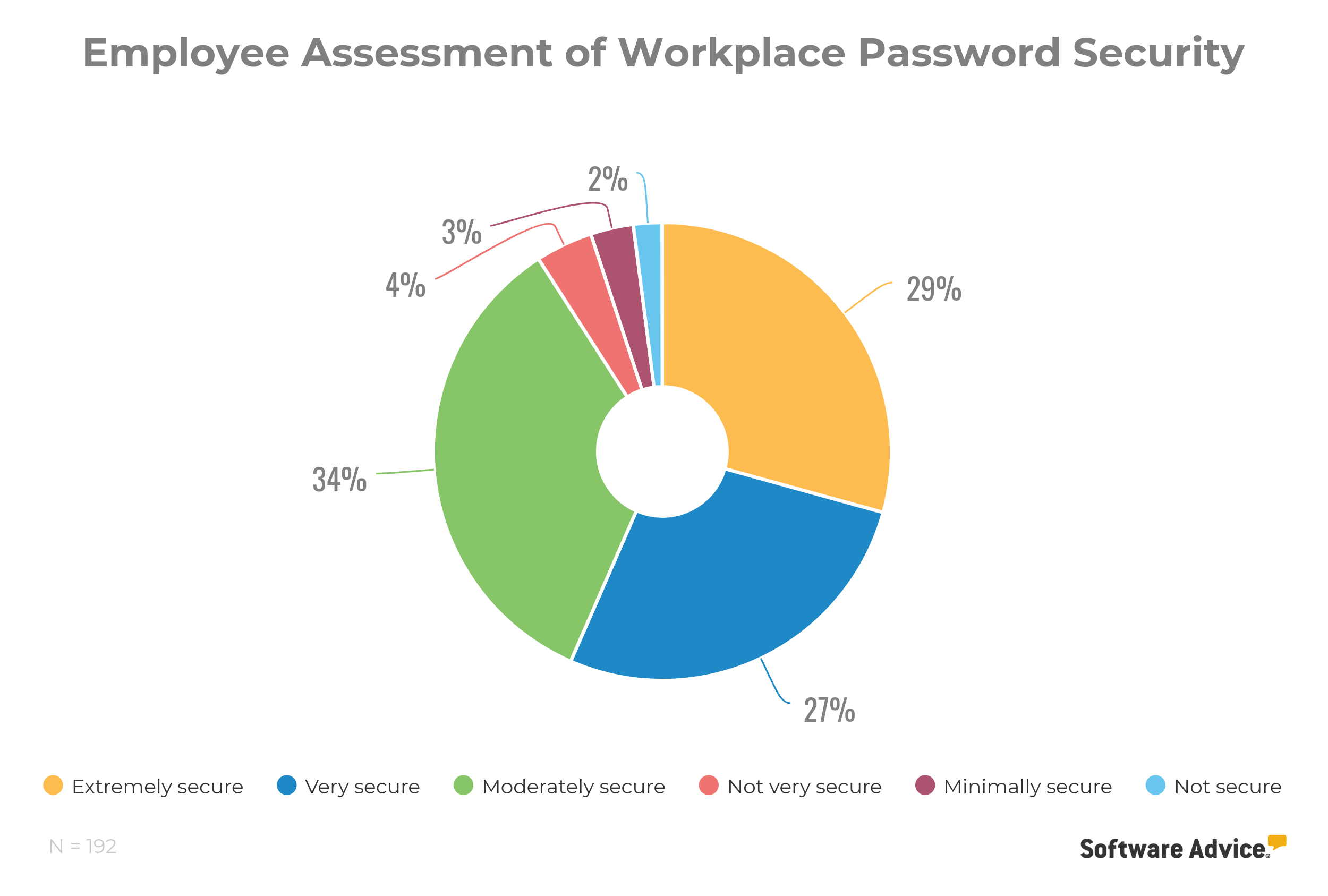
This includes, as much as anything, password hygiene—one of the best defenses against unauthorized access. Yet only 56 percent of employees consider their passwords “extremely secure” or “very secure,” according to a Software Advice survey.
To maintain sound password management, require that all users:
Use a combination of letters (capitalized and lowercase), numbers, and symbols. Sorry, pet names and birthdays are not effective safeguards (nor were they ever) against password theft. The longer and more complex it is, the better.
Update passwords at least once every six months. You might think your password is strong, but here’s the reality: Even seemingly impenetrable passwords, if left to languish, grow more susceptible over time. Regular updates will limit the volume and lifespan password-based security breaches, thereby preserving the integrity and security of your ERP system.
Create a unique password for every application. By logging in with the same password across all business applications, users jeopardize not only their ERP software, but every other system in use. Require instead that users create a unique password for each application they use.
Integrate identity management software as an extra line of defense
If you’re wondering how in the world you’re going to think up all these passwords, much less remember them, here’s the thing: You don’t have to.
Identity management software automatically generates unique, hard-to-crack passwords at the click of a button and stores them all in a secure and encrypted digital repository.
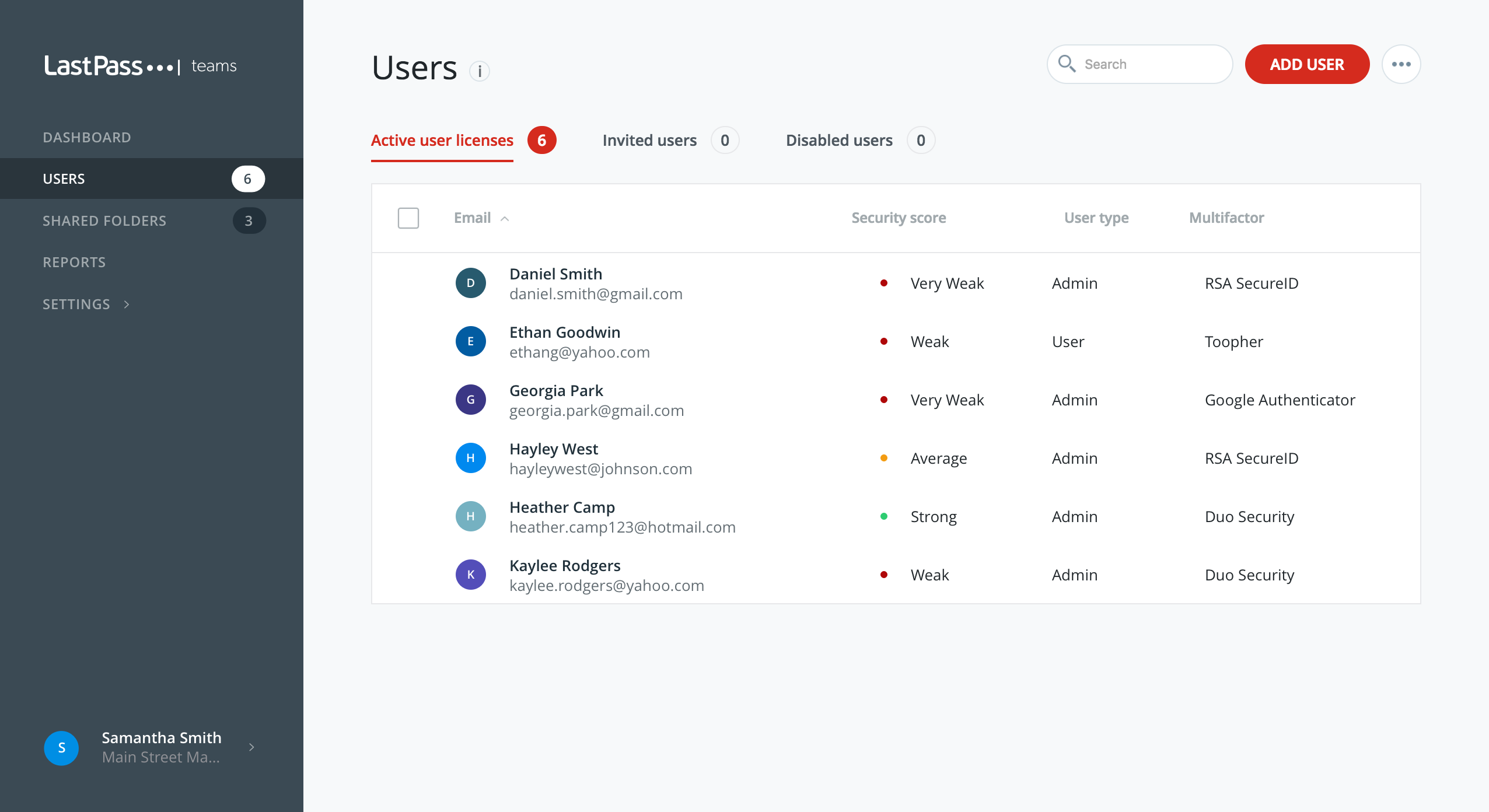

Active user licenses in LastPass Enterprise
But the benefits don’t end there. Many identity management applications automate ERP access control processes like user modification and access rights, boosting efficiency and freeing up your IT department to focus on quality assurance. It can even monitor user activity and enforce regulatory compliance based on a customizable set of parameters.
With many affordable and easily integrable options to choose from, identity management software is an invaluable line of defense against unauthorized access.
Prime your business for optimum access control
While the above recommendations pertain to all kinds of businesses, yours included, such structural change takes time and effort to implement. When it comes to protecting your data, though, time is of the essence.
Here are some things you can do right now to set your ERP access control plan in motion:
Review existing access control processes. Before you implement any changes, you have to know what changes to make. A thorough assessment of your existing protocol will allow you to identify existing gaps or vulnerabilities in your ERP’s access control, serving as a road map for any necessary logistical refinements.
Reinforce security best practices with ongoing ERP training. If you’re not regularly educating your users on the nuances of ERP software, your data is prone to mismanagement—regardless of how secure you think your system is. ERP training is essential to the success and security of your business, demanding a strategic approach—which we outline in this article—to maximize awareness and retention.
Give us a ring. If you’re on the fence about whether your current ERP system is sufficient to execute your plan, we’re here to help. Our friendly software advisors are always at the helm, ready to provide you with a range of software options catered to your data security aspirations. For a free 15-minute phone consultation, call (855) 998-8505.