Find the best Network Access Control Software
Compare Products
Showing 1 - 20 of 45 products
Sort by
Reviews: Sorts listings by the number of user reviews we have published, greatest to least.
Sponsored: Sorts listings by software vendors running active bidding campaigns, from the highest to lowest bid. Vendors who have paid for placement have a ‘Visit Website’ button, whereas unpaid vendors have a ‘Learn More’ button.
Avg Rating: Sorts listings by overall star rating based on user reviews, highest to lowest.
A to Z: Sorts listings by product name from A to Z.
NordLayer
NordLayer
NordLayer is a remote network access solution for modern companies, particularly suitable for SMBs searching for an effective and agile way to update legacy infrastructure and implement profound Secure Service Edge (SSE) practices...Read more about NordLayer
Banyan Security
Banyan Security
Banyan Security’s next-generation zero trust network access platform offers seamless remote access to corporate resources hosted on-premise or in hybrid and multi-cloud environments. Banyan enhances security by reducing your attac...Read more about Banyan Security
Portnox CLEAR
Portnox CLEAR
Portnox Clear is a cloud-based network access control solution that helps businesses monitor endpoint risks, detect compromised devices, and automate mitigation to high-risk devices. It allows staff members to configure essential ...Read more about Portnox CLEAR
Appgate SDP
Appgate SDP
Powered by Zero Trust Architecture, Appgate secure access and cybersecurity solutions enable businesses to reduce risk and ensure network security within a digital environment. Serving more than 1,000 organizations across 40 count...Read more about Appgate SDP
Device42
Device42
Device42 is an asset management solution that enables IT administrators to track hardware, software, devices and networks. The key features includes automated data center management, service management, device discovery, asset tag...Read more about Device42
Access Control Manager
Access Control Manager
Access Control Manager is a network access control solution that helps businesses in retail, healthcare, oil & gas, banking, utilities and other industries secure properties, assets and personnel. It lets supervisors monitor intru...Read more about Access Control Manager
Adept Secure
Adept Secure
Adept Secure is a network monitoring solution that provides businesses with tools to identify and prevent cybersecurity threats across enterprise networks. Professionals can track all incoming or outgoing traffic across websites a...Read more about Adept Secure
N-sight
N-sight
N-able N-sight™ RMM combines remote monitoring and management, remote access, ticketing, and billing capabilities, into one powerful yet easy to use platform that streamlines day-to-operations, combats threats and drives operation...Read more about N-sight
Genea Security
Genea Security
Genea Access Control is a cloud-based access control software designed to help small businesses to large enterprises ensure the security of access across building facilities. Key features include attendance reports, credential man...Read more about Genea Security
Kisi
Kisi
Kisi is a cloud-based physical security application that helps businesses control user access and exchange communications across organizational devices. Administrators can utilize a centralized dashboard configure door security ac...Read more about Kisi
Genian NAC
Genian NAC
Genian NAC is a network access control software designed to help businesses of all sizes detect IP-enabled devices and monitor asset information to manage vulnerabilities. The platform enables administrators to analyze heterogeneo...Read more about Genian NAC
Perimeter 81
Perimeter 81
Perimeter 81 is the first Cybersecurity Experience Platform to streamline SASE through its groundbreaking ease-of-use and unified network security stack. With a global network of PoPs, Perimeter 81 offers secure network capabiliti...Read more about Perimeter 81
Kentik
Kentik
Kentik is a cloud-based network management solution which assists network managers, network engineers and operators with data encryption and access control. Its key features include bandwidth monitoring, network diagnosis, perform...Read more about Kentik
Conecta Suite
Conecta Suite
Control access to Google Workspace (G Suite) in a few clicks. Create user groups with custom login and logout rules. Block the use of the corporate account by time and location. Control the accesses made by the browser, cell phon...Read more about Conecta Suite
strongDM
strongDM
strongDM is a database management software tool designed for SMBs and agencies. It aims to provide technical staff, including CTOs, CIOs, DevOps, and infrastructure engineers, secure access to their company's resources. It blends ...Read more about strongDM
Pulseway
Pulseway
Pulseway is an integrated IT assets and network monitoring solution designed for IT administrators to remotely monitor and control their business IT resources. The solution supports multi-deployment architecture, allowing the user...Read more about Pulseway
Foxpass
Foxpass
Foxpass is a cloud-based and on-premise platform that helps small to large enterprises automate threat detection and access control process across servers and networks. It provides local cache, which enables users to keep systems ...Read more about Foxpass
Brivo Access
Brivo Access
Looking for access control and proptech solutions to improve security and add technology to the building? Add cloud-based access control and make spaces smart with a platform that brings keyless entry, mobile credentials, remote s...Read more about Brivo Access
NACVIEW
NACVIEW
NACVIEW is a network access control solution that provides visibility and control over all devices connecting to an organization's network. NACVIEW is designed for mid-size to large enterprises across industries such as healthcare...Read more about NACVIEW
mmesh
mmesh
HYBRID CLOUD INTEGRATION MADE SIMPLE mmesh is an easy-to-use hybrid cloud integration platform that makes your architecture independent from the underlying infrastructure. mmesh lets you build your own virtual private topology a...Read more about mmesh
Popular Comparisons
Buyers Guide
Last Updated: March 16, 2023The increasing number of devices accessing corporate networks requires businesses to pay special attention to network security. However, deploying separate security solutions (antivirus, firewall, etc.) from different vendors can increase the complexity of network infrastructure and end up costing significantly on maintaining each of them.
Such challenges can be handled by deploying a centralized solution called network access control software. This software helps organizations keep unauthorized devices and users out of organizational networks. It controls who has access to what part of the network and helps track access details such as the time of access and the device used.
But given the many options available on the market, buying a network access control tool can be confusing. To help you figure out how to find the tool that matches your business needs, we’ve created this buyers guide that has all the essential information relating to network access control software.
Here’s what we'll cover:
What is network access control software?
Network access control software is a solution that helps organizations strengthen their network security by enforcing access policies for internal as well as external users and devices. These policies govern device authentication and endpoint configuration.
The solution grants users or devices access to organizational resources depending on the degree of authorization awarded to them. The right to grant, revoke, or block access on a case-by-case basis typically rests with the network administrators.
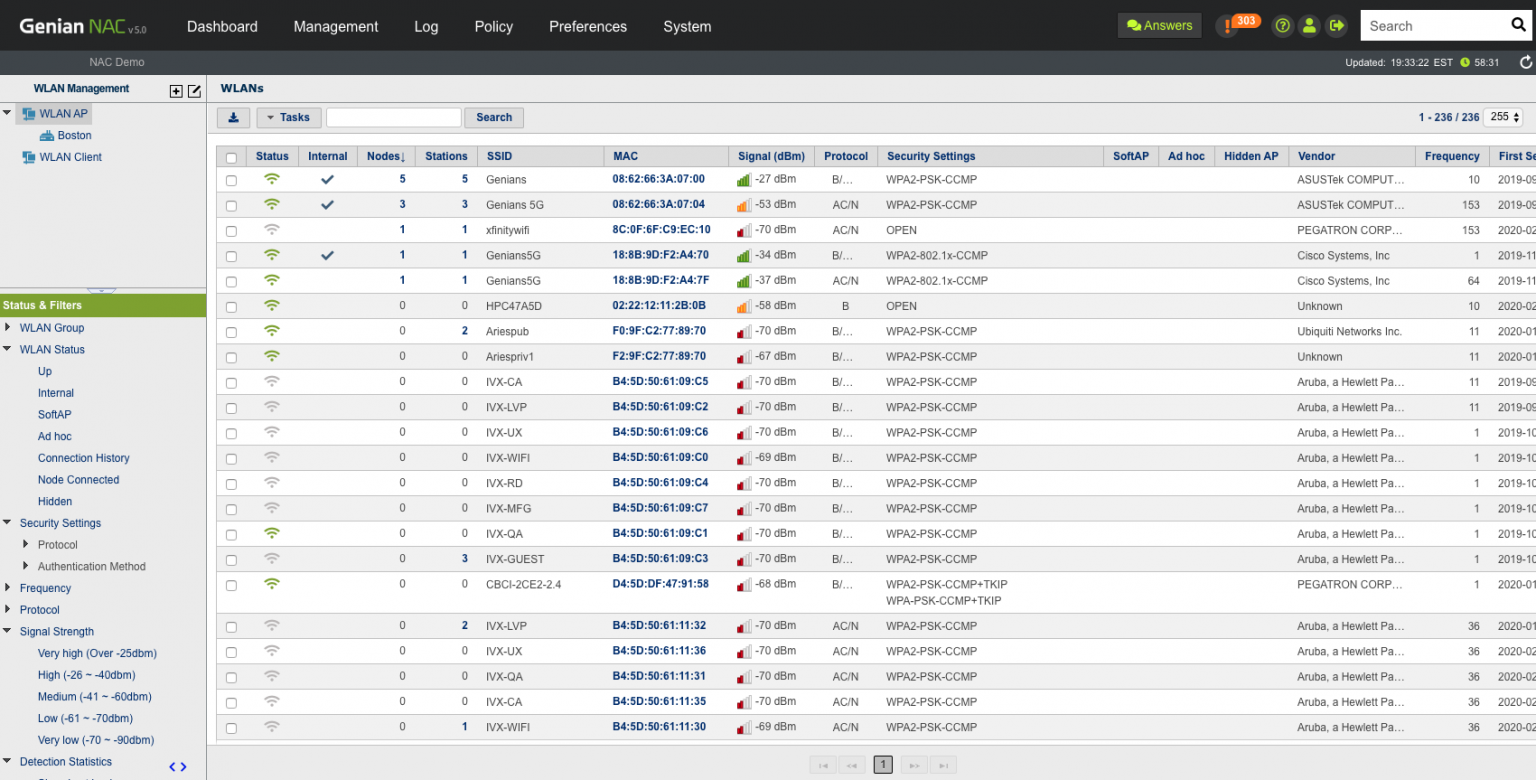
Network access control in Genian NAC Software (Source)
Common features of network access control software
The features vary by product or vendor but most network access control tools have the following in common:
Access controls/permissions | Authenticate and authorize individuals to access the information they are allowed to see and use based on their roles, devices, location, etc. |
Network security | Secure organization network by adopting preventive measures against unauthorized access, misuse, malfunction, modification, destruction, or improper disclosure. |
Policy creation | Define policies for network devices or users to follow in order to achieve business objectives. These include rules and specifications about how access to the network is managed, who may access information, and under what circumstances. |
Asset tracking | Track or scan all company-owned assets (in this case, devices) or those entering into the network, regardless of where they are located. This capability also allows blocking devices that show malicious behavior. |
Dashboard | Use a centralized dashboard to view insights into network traffic analysis, devices entering and leaving the network, suspicious behaviors, etc. |
Multiple authentication methods | Use more than one authentication method to authorize users to access company data, applications, and other resources via the organization network. |
Continuous monitoring | Continuously assess, discover, and classify users as they connect to the organizational network without disrupting business operations. This helps network and security administrators discover and mitigate security threats as and when they evolve. |
Multi-device support | Oversee all outside devices that join the network and access company resources. |
Third-party integration | Integrate with other third-party tools such as access governance tools and firewalls to enhance security policies. |
Remote access/control | Monitor and control access to the network from anywhere and at any time. This feature helps employees to work remotely while enjoying access to their organization’s computer or network. |
What type of buyer are you?
Before purchasing network access control software, you should assess which buyer category you belong to. The majority of buyers fall into the following categories:
Small and midsize businesses (SMBs) (up to 500 employees): SMBs need network access control to ensure the security of their organization network from outside devices and users. Due to budget constraints and lack of IT experts, they outsource some of their business processes such as accounting, IT services, and digital marketing to outside parties. This makes their network vulnerable to threats such as data breaches, noncompliances, and mishandling of sensitive information.
Investing in a network access control solution that has a low cost of implementation and features such as remote access control, authentication of devices, and incident response capabilities will be beneficial for buyers of this segment. This will help SMBs provide controlled access to users based on their role, device and location, and protect their data from outside attacks.
Large enterprises (over 500 employees): Unlike SMBs, large enterprises have a complex network infrastructure with a huge number of devices, applications, files, and other resources connected to each other. Additionally, such organizations are rapidly deploying internet of things (IoT) applications, automation and other IT initiatives related to data analytics—which means moving huge amounts of data over networks. This makes the security of IT networks essential for such organizations.
A fully featured network access control system that offers continuous monitoring of network access, encryption, and authentication features will be beneficial for this segment. They should opt for a tool that helps ensure all devices comply with organizational security requirements, sensitive information moving across are encrypted, and prevent unauthorized access to data.
Benefits of network access control software
Listed below are some benefits you can expect from using a network access control software tool:
Network visibility: Network access control solutions can help identify which devices exist on your network and who has access to them. The comprehensive view of the entire network allows administrators to detect the root cause of any issue and proactively assess them before they critically affect the organization’s infrastructure.
Achieving compliance: Network access control solutions help organizations meet compliance standards across many industries, such as HIPAA, SOX, NIST, and PCI-DSS. Network and security administrators can bring organization security policies into compliance with the help of such tools by conducting audits and checks on each user type, device type, and operating system.
Protect sensitive data: The aim of network access control solutions is to control access of devices and users to organization networks and infrastructure. This access control capability helps network administrators provide controlled or restricted access to data based on user role, time of day, location, application, etc.
Market trend to understand
Here’s a market trend to keep in mind when selecting a network access control software solution for your business:
The growing need for network access control software with the rise in bring your own device (BYOD): Nowadays, wireless networks and mobile technologies have introduced personal devices (via BYOD) into the workplace. Many businesses have also adopted the remote working trend. These businesses will need controls to ensure users and devices do not compromise the safety of the network. This has accelerated the need for network access control solutions to control outside devices and remote workers by ensuring they are configured for proper data protection.
Note: The application selected in this article is an example to show a feature in context and is not intended as an endorsement or recommendation. It has been obtained from sources believed to be reliable at the time of publication.







