Best Container Security Software of 2026
Updated October 14, 2025 at 4:11 AM
Written by Priyanka Aggarwal
Senior Market Research Specialist
Edited by Rina Rai
Senior Editor
- Popular Comparisons
- Buyers Guide
Compare Products
Showing 1 - 25 of 45 products
Compare Products
Sort by
Reviews: Sorts listings by the number of user reviews we have published, greatest to least.
Average Rating: Sorts listings by overall star rating based on user reviews, highest to lowest.
Alphabetically (A-Z): Sorts listings by product name from A to Z.


Secure your code, cloud, and runtime in one central system. Aikido’s all-in-one security platform is loved by developers and se...Read more about Aikido Security


Fidelis Halo is a cloud-native application protection (CNAPP) platform that helps businesses secure servers, containers, and clo...Read more about Fidelis Halo

Designed with Fortune 500 and Global 2000 companies in mind, SentinelOne is a leading autonomous cybersecurity platform speciali...Read more about SentinelOne
SentinelOne's Best Rated Features
See All
SentinelOne's Worst Rated Features
See All

Designed for organizations operating in the cloud who need complete, centralized visibility of their entire cloud estate and wan...Read more about Orca Security
Orca Security's Best Rated Features
See All
Orca Security's Worst Rated Features
See All

Unify SIEM, endpoint security, and cloud security Elastic Security modernizes security operations — enabling analytics across ye...Read more about Elastic Security
Elastic Security's Best Rated Features
See All
Elastic Security's Worst Rated Features
See All

Docker is an on-premise and cloud-based application development platform that helps businesses build, test and share containeriz...Read more about Docker
Docker's Best Rated Features
See All
Docker's Worst Rated Features
See All

PingSafe is an industry-leading all-in-one cloud security platform with a comprehensive knowledge of the attackers’ modus operan...Read more about PingSafe

Xygeni Security is an AI-powered Application Security Posture Management (ASPM) platform built for organizations securing modern...Read more about Xygeni Security

Embrace a new era of cloud infrastructure management with Appvia Wayfinder, designed to convert complexity into simplicity, and ...Read more about Appvia Wayfinder

Google Container Security is a cloud-based solution that helps businesses secure container environments across Anthos, Google Ku...Read more about Google Container Security

Tenable.io is a cloud security solution that helps businesses in the energy, transportation, automotive, education, retail, fina...Read more about Tenable Vulnerability Management

The Uptycs CNAPP + XDR Platform is a comprehensive security solution designed for modern attack surfaces. Uptycs enables organiz...Read more about Uptycs

Argon’s first-to-market holistic security solution protects the integrity of software development environments’ CI/CD pipelines,...Read more about Argon

Lacework is a cloud-based platform that provides intrusion detection, compliance and automated threat defense for multi-cloud co...Read more about Lacework

Wiz enables organizations globally to rapidly identify and remove critical risks in cloud environments. Wiz secures everything ...Read more about Wiz

Designed for businesses in retail, marketing, education and other industries, Platform.sh is a cloud-based solution that helps s...Read more about Platform.sh

CrowdStrike is a cloud-based endpoint protection solution, which assists small to large businesses with anti-virus protection an...Read more about CrowdStrike
CrowdStrike's Best Rated Features
See All
CrowdStrike's Worst Rated Features
See All

Designed for businesses in banking, information technology, financial services and other industries, OX Security is a cloud secu...Read more about OX Security

Spectral Enables teams to build and ship software faster while avoiding security mistakes, credential leakage, misconfiguration ...Read more about SpectralOps

Modern software application development has evolved from deploying products periodically to build them on a daily or hourly basi...Read more about Artifactory
Artifactory's Best Rated Features
See All
Artifactory's Worst Rated Features
See All

Cisco Secure Firewall is a cloud-based firewall system that provides security across hybrid and multi-cloud environments. Cisco...Read more about Cisco Secure Firewall

Conviso Platform is an Application Security Posture Management (ASPM) solution that centralizes the management of risks, vulnera...Read more about Conviso

StackRox is a Kubernetes and container security platform, which helps businesses and government agencies protect cloud applicati...Read more about StackRox

WhiteSource is the leading solution for agile open source security and license compliance management. It integrates with y...Read more about Mend

Heroku is a cloud-based application development platform that supports multiple programming languages. It helps developers effec...Read more about Heroku
Heroku's Best Rated Features
See All
Heroku's Worst Rated Features
See All
Popular Comparisons
Buyers Guide
This detailed guide will help you find and buy the right container security software for you and your business.
Last Updated on October 14, 2025Containers are standard software packages used to build, test, and deploy applications on multiple environments. They include all the required executables, binary codes, libraries, and configuration files except the operating system image. This makes them lightweight and portable. Also, they offer agile deployment capabilities and need less coordination and oversight than on-premise or virtualization infrastructure.
Despite these benefits, containers create security challenges. You have to secure the container host, the applications within the container, and the container management stack, among others. To address these security issues, you can use a container security software platform.
Container security software scans containers for vulnerabilities and policy violations and provides remediation for any identified threats. It’s used to secure the various components of containerized applications, such as container images and code repositories, along with their infrastructure and connected networks.
In this buyers guide, we explain what container security software is, its common features and benefits, and the considerations and trends you should keep in mind during software selection.
Here's what we'll cover:
What is container security software?
Container security software is a software tool that helps businesses manage and secure containerized files, applications, systems, and their supporting networks. It protects the cloud computing infrastructure running containerized applications from vulnerabilities in the IT environment. It simulates attacks from common threat actors to detect container vulnerabilities more thoroughly rather than simply relying on standard security scans.
The software provides centralized information about the entire container environment, including details of the docker engine and client, plugins, image registries, and image metadata. It also has an access control mechanism that allows administrators to decide which users can access the containerized data and apps.
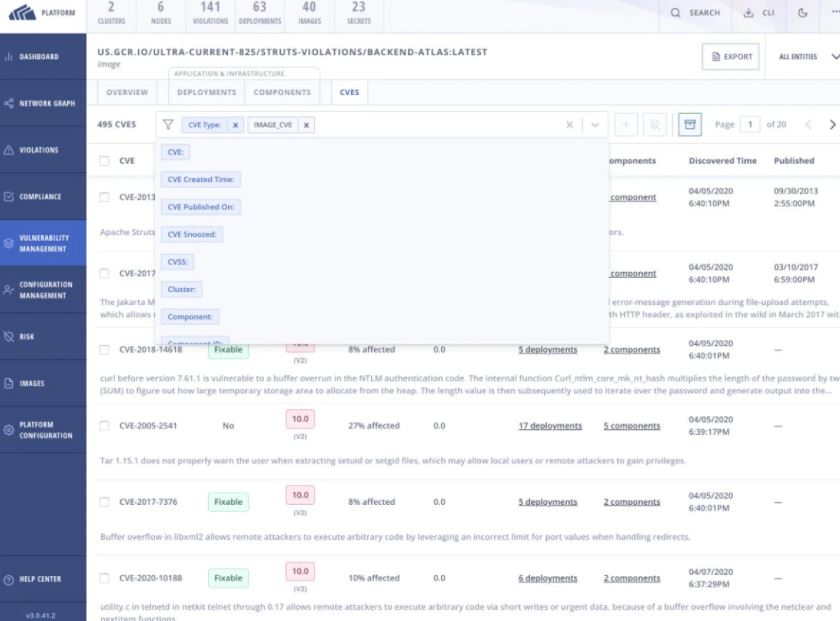
Security vulnerability management in StackRox (Source)
Common features of container security software
Here are some common features of container security software:
Container scanning | Scan container images or pods deployed to production for vulnerabilities or compliance issues. |
Vulnerability management | Detect, classify, prioritize, and mitigate threats and vulnerabilities to your containerized applications. |
Policy management | Enforce security policies to block the use of container images that are vulnerable to threats or incidents. |
Continuous integration (CI) | Integrate the software with container registries and orchestration platforms. CI establishes a consistent and automated way to build, package, and test applications. |
Container inventory visibility | Gather topographic information about container projects—images, image registries, deployments, runtime behavior, and containers spun from the images—to get complete visibility into your container inventory. |
Runtime security | Ensure security during the runtime phase of deployment. This added layer of security helps detect and respond to security threats to the containers running in your environment. |
Compliance | Address security challenges in containers to ensure they’re compliant with standards such as the Center for Internet Security (CIS) and Service Organization Control 2 (SOC 2) benchmarks. |
Security alerts | Receive real-time security alerts when new issues are reported or when vulnerable components are added to your container stacks. |
Priority scoring | Assess security risk across your IT environment and assign priority scores to them to focus your remediation efforts. |
What type of buyer are you?
Understanding the different types of buyers will help you identify your needs better and make an informed purchase. The majority of buyers in the container security market belong to one of the following categories:
Small and midsize enterprises (up to 500 employees): Small and midsize businesses (SMBs) have fewer users and IT assets compared to large enterprises and a strict security budget to follow. They need a tool that can regularly scan their container infrastructure for common and potential threats and vulnerabilities. They should opt for an open source container security system with auditing functionality to detect vulnerabilities early on in the app development process. Cloud-native tools that don't require substantial investment for infrastructure maintenance would be a good choice for these buyers. Container scanning, policy-based admission control, and vulnerability management are a few recommended features for this category.
Large enterprises (over 500 employees): Large enterprises have more users and IT assets than SMBs. Therefore, their container security needs are more extensive. These buyers also have the resources and budget to invest in advanced IT security. They should opt for a full-featured container security suite to ensure protection across the container lifecycle. Automatic vulnerability detection; containerized application security from build time to runtime; integration with container security options; support for different container formats; and active threat prevention across servers, containers, and other microservices are some advanced features they should look for.
Benefits of container security software
Listed below are the key benefits of using container security software:
Better visibility into potential threats: Cybercriminals are coming up with new ways to break into business networks, and container security software helps you stay up to date with these new developments. It offers the ability to detect and prevent security breaches even during runtime and protects your organization against the evolving threat landscape. It also sends real-time security alerts when new issues are reported or when vulnerable components are added to your container stacks.
Secure application development: The tool’s image scanning feature ensures that the containers you use as building blocks during application development are reliable and secure against common threats. It scans the container contents to look for issues ahead of development and also performs checks before the containers are deployed to production. It’s an automated process that helps identify issues as you develop your application and its containers.
Remediation based on threat urgency: Container security software assesses risks across the IT environment and assigns a priority score to each risk. It offers an in-depth analysis of the vulnerabilities in your network, the potential threats they can cause, their level of urgency, and how they can be resolved. Based on this analysis, you can prioritize your remediation efforts to first attend to the most critical vulnerabilities.
Key considerations
Let’s go through a few considerations you should keep in mind when selecting a container security tool:
Functionality: Assess your security needs and decide if you need a tool for container scanning, for serverless function scanning, or for both. For serverless security, the software you select should work well with the serverless computing services that you’re already using, such as AWS Lambda or Azure Functions. And for container security, you’ll have to ensure the software runs smoothly with container deployment tools such as Docker and Kubernetes.
Integration options: The container security solution you choose should integrate well with your existing enterprise security software and practices, such as security information and event management (SIEM) and identity management tools, DevOps practices, and container registries. An integrated tool will provide a feedback loop to shift left (i.e., scan and analyze container images early in the DevOps process), offering continuous guidance to your development and operations teams.
Infrastructure protection: Containers help implement workload-level security, but they also introduce new infrastructure components and unfamiliar attack surfaces. Therefore, ensure you select a container security solution that secures the cluster infrastructure and orchestrator as well as the containerized applications they run. Also, check if the tool is compliant with regulations such as the National Institute of Standards and Technology (NIST) 800-53 and Payment Card Industry Data Security Standard (PCI DSS).
Market trends to understand
Here’s a recent trend in the container security software market that you should be aware of:
Container scanning is emerging as a security best practice for DevOps. Developers are looking for ways to deliver a faster continuous integration and continuous delivery (CICD) pipeline. Container scanning is becoming a part of this “shift left” strategy that supports scanning and analyzing container images early on in the DevOps process to identify vulnerabilities. This reduces the number of tools used and streamlines operations and controls that are built in from the start. Organizations can use these security tools during the pre-deployment phase to address potential security risks and make it safely into production. Because of these benefits, the container scanning approach is emerging as a security best practice for DevOps.
Note: The application selected in this guide is an example to show a feature in context and is not intended as an endorsement or a recommendation. It has been taken from sources believed to be reliable at the time of publication.